Amount Cannot Be Specified Before Negotiations Begin
"If Data Was Taken, It's Almost Certainly Personal Information" ... Expert Warning
Blackmail Risk Remains Even After System Restoration
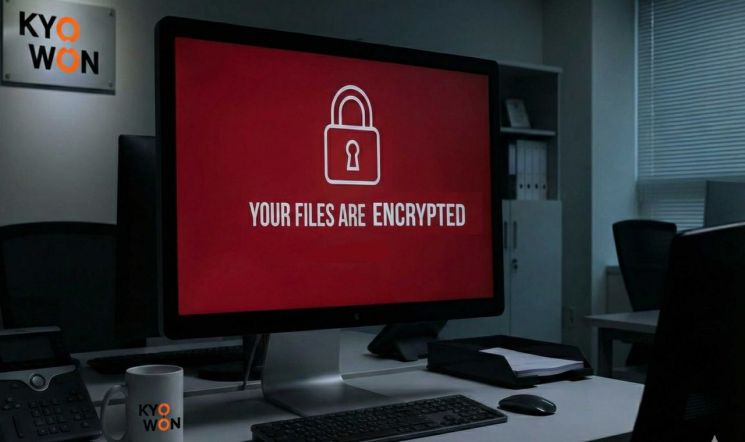
Although Kyowon Group's hacking report to the government explicitly stated that there was a threat from the hacker, the amount demanded by the hacker was listed as '0', drawing attention to the background of this situation. The company's services were restored using backup servers, and there has been no financial damage so far. However, the cybersecurity industry believes it is highly likely that the hacker stole personal information. This suggests the possibility of a 'double extortion' method, in which the hacker both encrypts the system and exfiltrates internal data to use as leverage for threats.
According to cybersecurity authorities and industry sources on January 15, this is a common initial extortion tactic in hacking attacks. While some hackers immediately present a ransom demand upon intrusion, in many cases, they first leave a message instructing the victim to "make contact," thereby steering the company into negotiations. Channels for negotiation often include dark web-based chat platforms or specific email addresses. From the company's perspective, at the time of reporting the incident, no monetary discussions have taken place yet, making it impossible to specify a demanded amount, which is why the ransom amount is listed as '0' in the report.
Kyowon Group's incident report also specifies that there was a threat, but both the 'hacker's demanded amount' and the 'expected damage amount' are recorded as '0 (KRW)'. This is interpreted not as an indication that the hacker did not demand money, but rather that no amount has been presented yet or negotiations have not progressed to that stage.
Kyowon Group reported signs of a data breach to the Korea Internet & Security Agency (KISA) and the Personal Information Protection Commission, but maintains that it is still "under review" whether the leaked data included personal information. However, the cybersecurity industry believes that after infiltrating a system, hackers can scan servers to distinguish between those storing personal information and those that do not. If there is evidence that data was exfiltrated, it is likely that the hacker selectively took data containing personal information rather than meaningless information. Kyowon Group, which operates not only educational services but also travel and lifestyle businesses, holds large volumes of personal data on customers, students, and parents.
The reason hackers target personal data among various types of information is straightforward. What companies fear most is not simply system paralysis, but the fines and reputational damage resulting from personal data leaks. Especially for companies like Kyowon Group, which operate educational, travel, and lifestyle businesses, the volume of customer, student, and parent information is significant. If such data is leaked externally, the company faces not only legal liability but also major damage to its image. Using personal data as leverage for threats is a much more powerful pressure tactic than simply encrypting systems and halting operations.
Lee Hyungtaek, Director of the Korea Ransomware Response Center, stated, "Hackers have multiple options, such as carrying out a second attack or releasing stolen data on the dark web if negotiations break down. Even if services are restored through backups, as long as the hacker possesses the data, the company remains vulnerable to ongoing threats."
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.
![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)














