Four Types of Information for USIM Cloning and 21 Types of Management Data Leaked
No Possibility of Personal Information Leakage Such as Names, Addresses, or Resident Registration Numbers
"Impossible to Make Calls, Send Texts, or Steal Financial Assets Using Cloned Phones"
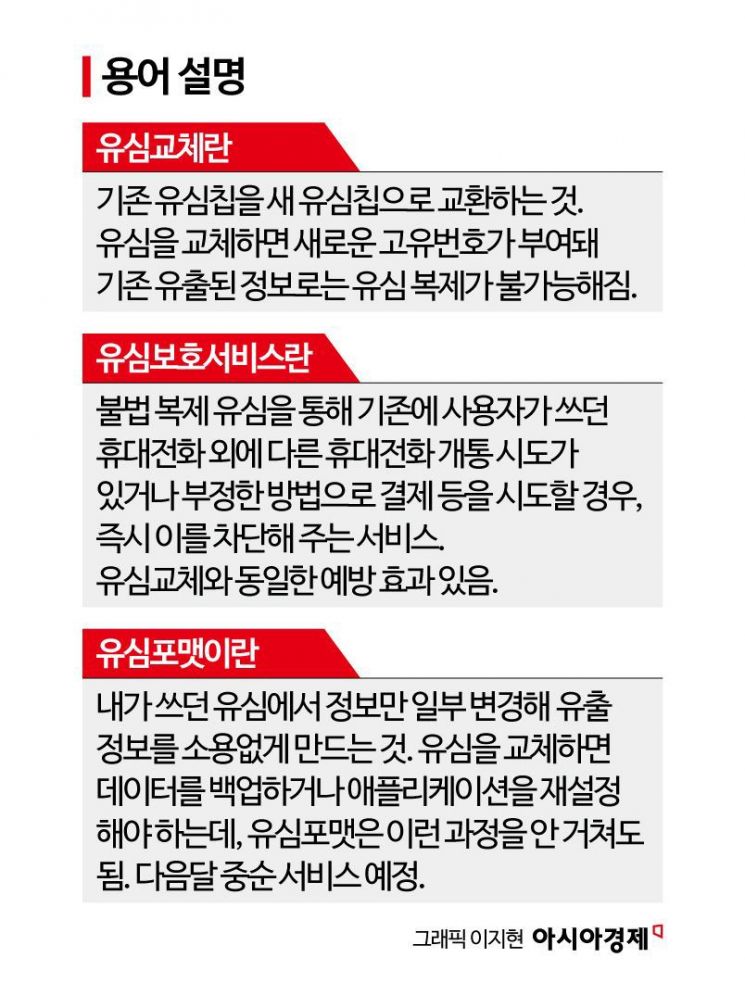
SKT to Launch USIM Format Service Next Month
"Expected to Have the Same Effect as USIM Replacement
Much More Convenient Without Data Backup"
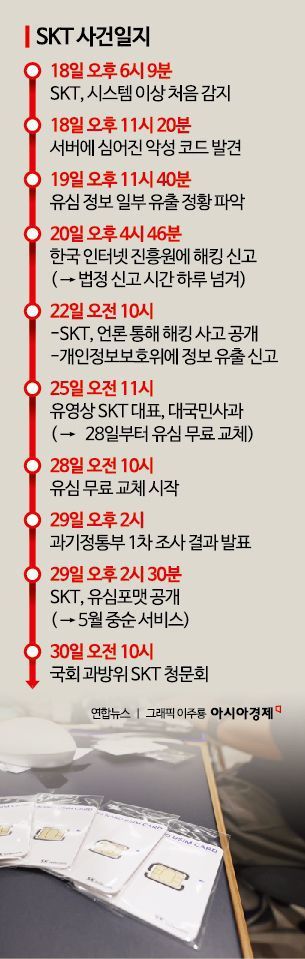
On April 30, SK Telecom, political circles, and the government were busy clarifying the exact circumstances of the hacking incident and preparing countermeasures for the 25 million affected users, including those with budget phone plans. That morning, SK Telecom CEO Yoo Youngsang appeared before a National Assembly hearing to explain the hacking incident, 12 days after the USIM hacking crisis began. Minister of Science and ICT Lee Jongho visited SK Telecom’s headquarters to urge the company to prepare measures for affected customers. However, the government focused on minimizing the fallout from the incident, emphasizing that there had been no additional leakage of personal information.
The Ministry of Science and ICT announced in its first investigative report on April 29 that “so far, the only information leaked in connection with the hacking incident was USIM-related data, and no personal information such as names, addresses, emails, or resident registration numbers of subscribers was leaked.” The ministry also stated that the probability of discovering any personal information leakage in future investigations is essentially zero.
A senior official from the Ministry of Science and ICT told Asia Economy, “In addition to the five servers that were the subject of the first investigation, we are currently expanding the investigation to other servers, but there has been no leakage of personal information such as resident registration numbers or copies of identification documents,” adding, “There is no possibility that personal information will be found to have been leaked in further investigations.”
"No Possibility of Personal Information Leakage"
The Ministry of Science and ICT investigated five SK Telecom servers that showed signs of attack during its first week-long investigation from April 22 to April 29. The investigation confirmed that four types of information that could be used for USIM cloning, such as phone numbers and subscriber identification keys (IMSI), as well as 21 types of management information necessary for processing USIM data, had been leaked.
However, since there was no leakage of personal information or device unique identification numbers (IMEI), the government explained that “SIM swapping”?the illegal act of cloning a USIM using stolen information and inserting it into another phone?was not possible in this case. An official from the Ministry of Science and ICT in charge of the investigation stated, “In theory, it would be possible to combine the information leaked from SK Telecom to clone a USIM,” but added, “Crimes such as intercepting calls or texts or stealing financial assets by creating so-called ‘cloned phones’ with a copied USIM are impossible because SK Telecom operates an ‘abnormal authentication attempt blocking system (FDS).’”
The FDS is designed to detect and block cloned phones in advance. For example, if the USIM of a subscriber using a Galaxy smartphone is suddenly connected to an iPhone, or if a device that had been communicating with a base station in Seoul suddenly attempts to connect to a base station in Busan, the system detects this as an anomaly and blocks all phone activity.
"If USIM Format Is Properly Implemented, It Will Have the Same Effect as USIM Replacement"
In response to the recent USIM replacement crisis, SK Telecom announced that it is developing a “USIM format” technology, which will have the same effect as replacing a USIM, and plans to launch it in mid-May. Following the USIM protection service and USIM replacement, this is the third measure the company has introduced. The USIM format technology changes some of the information on a USIM used in a subscriber’s phone, making it different from the leaked information. This means the same effect as replacing the USIM can be achieved without physically changing it. An SK Telecom official explained, “When you replace a USIM, you have to back up data or reset applications, but the USIM format eliminates the need for such processes.” In fact, some SK Telecom subscribers experienced inconvenience when the balance on prepaid transportation cards such as “T-money” was displayed as zero after replacing their USIM. Prepaid transportation cards use near-field communication (NFC) to store information on the USIM and process payments, so they could not function properly after a USIM replacement.
Jang Hangbae, a professor in the Department of Industrial Security at Chung-Ang University, said, “Some verification is needed, but if the USIM format is properly implemented, it should be as safe as a USIM replacement.”
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.


![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)














