Abandoning Indiscriminate Hacking, Focusing on Large-Scale Targets
Dispersed Transfers After Six Weeks of Waiting... Money Flows Designed to Evade Tracking
Operations Leveraging Southeast Asian Payment Networks
North Korea, which has been funding its nuclear and missile development through virtual asset hacking, is changing its cyberattack tactics. Instead of indiscriminate attacks, it has shifted its strategy to focus its capabilities on large-scale targets with a higher probability of success. Although the number of attacks has decreased, the amount stolen in each incident has grown, and the money laundering process has become more sophisticated, cleverly evading international monitoring systems.
According to the security industry on December 21, the American blockchain analysis company Chainalysis recently reported that North Korea-linked hacking groups have stolen approximately $2.02 billion worth of virtual assets this year. This figure represents a 51% increase compared to the previous year, marking the largest amount ever recorded. In contrast, the total number of attacks decreased by about 74%, highlighting a clear 'selective attack' strategy. In fact, North Korea accounted for 76% of the total amount stolen from virtual asset services worldwide this year.
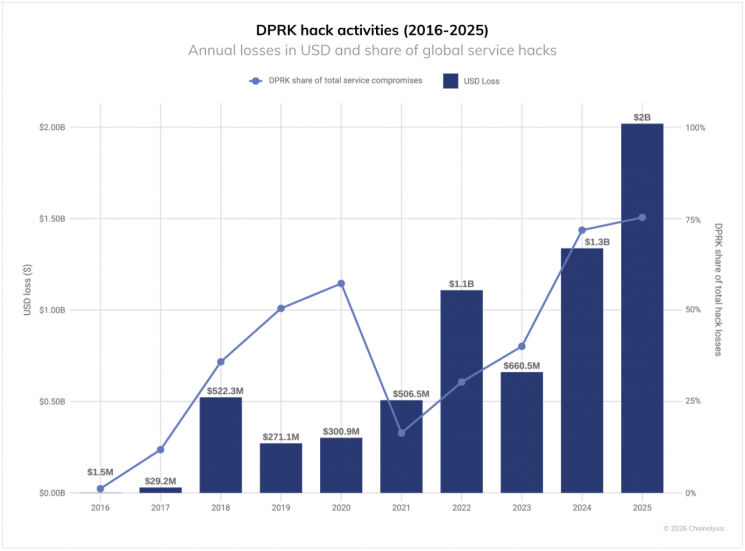 The American blockchain analysis company Chainalysis recently reported that North Korea-linked hacking groups have stolen approximately $2.02 billion worth of virtual assets this year, a 51% increase compared to the previous year. Image source=Chainalysis
The American blockchain analysis company Chainalysis recently reported that North Korea-linked hacking groups have stolen approximately $2.02 billion worth of virtual assets this year, a 51% increase compared to the previous year. Image source=Chainalysis
In the past, North Korea mainly targeted vulnerable decentralized finance (DeFi) bridges, but has recently returned to focusing on centralized exchanges such as Upbit and Bybit, as well as core infrastructure. Chainalysis analyzed that North Korean hackers are concentrating their efforts on so-called 'big fish'-targets that, after months of analysis, can yield hundreds of millions of dollars in a single attack. The $1.5 billion Bybit hack that occurred in February is a representative example.
Distinctive North Korean patterns have also been detected in money laundering methods. More than 60% of the stolen assets are split into amounts of $500,000 or less and dispersed to numerous wallet addresses, a strategy designed to evade the monitoring systems of exchanges and investigative agencies that focus on large transactions. The report noted that North Korea typically completes its initial money laundering phase within about 45 days after a hack, and tends to move the funds in earnest only after the initial period of intensive monitoring has passed.
In particular, the Cambodia-based payment group Huione has been identified as a key hub for North Korean money laundering. The U.S. Department of the Treasury's Financial Crimes Enforcement Network (FinCEN) designated Huione as a major money laundering concern this year. Investigations revealed that the Huione Group laundered at least $4 billion in illegal funds from 2021 to early 2025, with a significant portion linked to North Korea's cyberattacks.
Experts assess that North Korean hacking has evolved beyond technical infiltration into a state-level financial operation that combines social engineering techniques. Recently, there has been a rise in cases where hackers impersonate recruiters from global IT companies to approach developers, then distribute malicious code or steal internal access rights. Chainalysis emphasized that the virtual asset industry must move beyond traditional transaction amount-based monitoring and strengthen its ability to detect North Korea's unique patterns of small, split remittances and geographic fund movements in real time.
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.

















