SKT Plans to Supply 15 Million USIM Cards in Three Months
Government and Experts: "Only USIM Replacement Ensures 100% Safety"
SKT: "Cloned Phones Technically Difficult to Create"
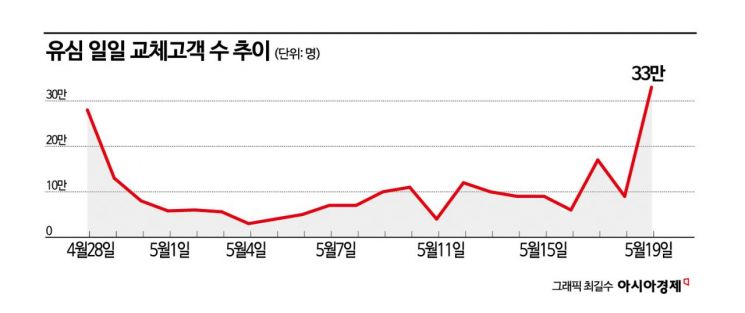
Amid growing concerns over cloned phones due to the hacking of SK Telecom's USIM (Universal Subscriber Identity Module) cards, the number of people who replaced their USIM cards reached 330,000 on May 19. This is the highest daily figure since SK Telecom began offering free USIM replacements on April 28, following the hacking incident. As both the government and experts stated that replacing the USIM card is necessary to fundamentally block the risk of cloned phones, a large number of anxious subscribers flocked to SK Telecom retail stores.
However, there is still a long way to go before all users have replaced their USIM cards. As of May 19, the cumulative number of USIM replacements stood at 2.52 million, which is about 10% of SK Telecom's total subscriber base of 25 million, including MVNO (Mobile Virtual Network Operator) users. SK Telecom previously announced plans to secure up to 15 million USIM cards from May through July. An SK Telecom official stated, "This figure represents the maximum number of USIM cards that can be secured at present." Even if all of these are supplied smoothly within three months, around 10 million more USIM cards would still be needed to achieve a complete replacement for all users.
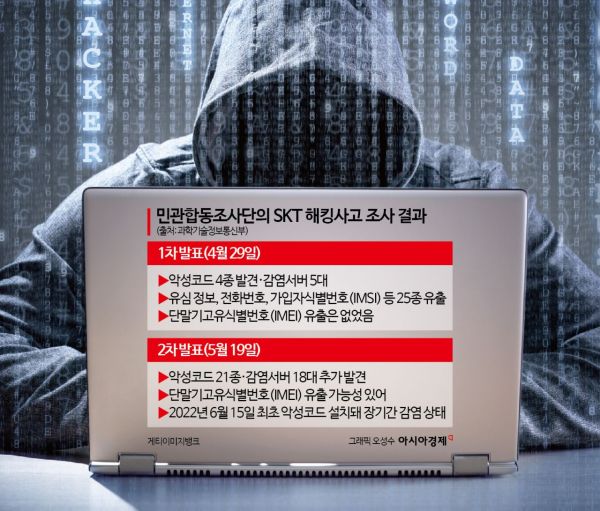
The reason USIM replacement has come under renewed focus a month after the hacking incident is because the government, in its second investigation report, raised the possibility that SK Telecom subscribers’ device IMEI (International Mobile Equipment Identity) numbers may have been leaked. The IMEI is a unique identifier assigned to each device and is a key element in creating cloned phones. Choi Kwangki, director at the Ministry of Science and ICT, stated, "At present, physically replacing the USIM card is the safest measure to prevent the risk of cloned phones," adding, "'USIM reconfiguration' and 'switching to eSIM' are technically equivalent to replacing the USIM, so consumers can choose whichever method is most convenient for them."
Experts emphasized that if the IMEI has been leaked, replacing the USIM card is the only ultimate solution. The USIM protection service that SK Telecom proposed as an alternative to replacement, in an effort to ease subscriber concerns, may not function properly if the IMEI is leaked. The USIM protection service is a system that allows a subscriber’s USIM information to work only on a single device. Even if a hacker creates a cloned USIM with stolen information and tries to use it in another device, the different IMEI would prevent the creation of a cloned phone. However, if the hacker also obtains the IMEI, the situation changes. In the worst-case scenario, if the hacker clones the device itself, it would be possible to create a so-called "twin phone."
Kim Myungjoo, professor at Seoul Women’s University’s Department of Information Security, also stated, "In theory, cloning is possible if the IMEI is leaked, and in the worst case, a cloned phone could be created," adding, "Considering the possibility of an IMEI leak, the USIM protection service alone is insufficient." Yeom Heungyeol, professor at Soonchunhyang University’s Department of Information Security, similarly said, "If the IMEI has also been leaked, only USIM replacement or USIM reconfiguration can be a fundamental solution."
However, SK Telecom maintains that it is physically impossible to create a cloned phone even if the IMEI is leaked. The company explained that there are multiple layers of security involved in the process of creating a cloned phone. An SK Telecom official stated, "The key value for authenticating IMEI information is held by each device manufacturer, so when an attempt is made to clone a phone on a different device, the process of authentication by the device manufacturer can filter out any cloning attempts," adding, "Even if, by chance, the device manufacturer’s authentication is bypassed, the authentication by the mobile carrier must also be passed."
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.

![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)














