AhnLab has discovered a phishing attack disguised as ‘Netflix subscription renewal and account verification’ and urged users to be cautious.
The attacker first distributed a phishing email titled ‘Your Subscription is about to expire.’ The email contained a malicious URL including the word ‘netfix,’ which is similar to netflix.
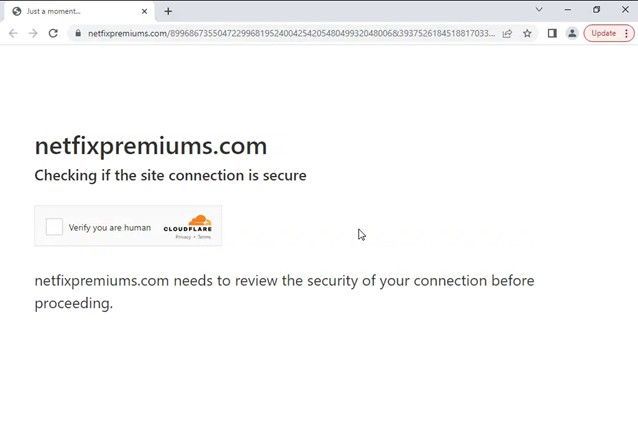
When users click the URL, they are not immediately directed to an information-stealing phishing site but instead are taken to a fake security verification page displaying the message ‘Verify you are human.’ This is presumed to be a step to avoid raising users’ suspicion.
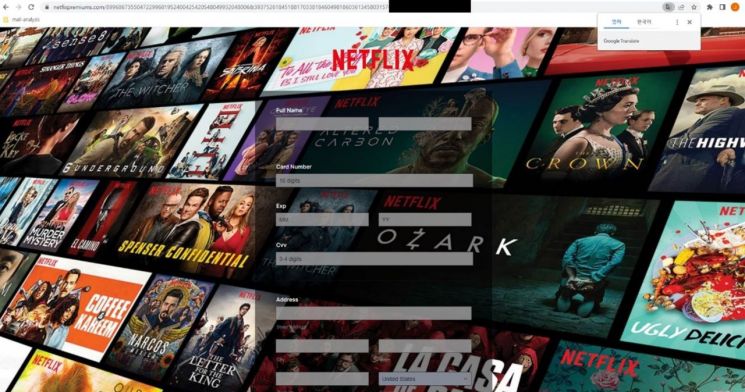
If users check the ‘Verify you are human’ checkbox on this page, they are redirected to a phishing site designed to resemble the Netflix login screen. This phishing site prompts users to enter their username, credit card information (card number, expiration date, CVC number), and address. If users unknowingly input the requested information, it is sent to the attacker. Leakage of this information can lead to secondary damages such as credit card fraud.
To prevent damage from phishing emails, users should ▲carefully verify the email sender ▲avoid opening attachments or clicking URLs in suspicious emails ▲keep antivirus programs like V3 updated to the latest version and enable phishing site blocking features ▲maintain the latest versions and security patches of all used programs (OS, internet browsers, office software, etc.) and follow basic security guidelines.
AhnLab detected and analyzed this case using an AI-based phishing email detection model built on various phishing email samples. AhnLab V3 diagnoses the phishing page URLs used in this attack, and the sandbox-based advanced persistent threat (APT) response solution ‘AhnLab MDS’ blocks the related emails.
Jeon Je-min, Senior Researcher of AhnLab’s Artificial Intelligence Team, said, “This attack used a sophisticated method by passing through a fake security verification page before redirecting to the phishing site to avoid user suspicion. Since attacks impersonating other popular services may emerge in the future, users must strictly follow basic security rules, such as not opening attachments or clicking URLs in suspicious emails.”
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.
![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)














