Targeting Victims' Absence to Remotely Reset Devices
Sending Malicious Files to Contacts via Hijacked Accounts
"Power Off When Leaving and Always Cover Your Webcam"
Many people leave their PCs powered on simply out of convenience. However, experts have issued a warning that this habit can lead to serious security threats. There is evidence that North Korean-backed hacking groups have remotely controlled individuals' smartphones and PCs to launch cyberattacks that completely wipe out key data such as photos, documents, and contacts. The hackers reportedly used webcams attached to PCs to check whether victims were away from home before carrying out their cyberattacks.
North Korean Hacking Groups Launch 'System Freeze' Attacks, Taking Over Smartphones, PCs, and KakaoTalk
According to a threat analysis report released on November 11 by Genius Security Center, a cybersecurity firm, there have been cases where cyber attackers, strongly suspected to be backed by North Korea, have gone beyond stealing personal information to cause direct harm in the real world by targeting smartphones, tablets, and PCs.
The report states that on September 5, a hacker reset the smartphone of a domestic psychological counselor and, using the hijacked KakaoTalk account, sent multiple malicious files disguised as a "stress relief program" to the victim's contacts.
On September 15 of the same month, an Android smartphone belonging to a North Korean human rights activist was also reset, and a malicious file was simultaneously distributed to 36 contacts via the hijacked KakaoTalk account. The spread of malicious code through KakaoTalk messages was analyzed as a typical North Korean social engineering-based hacking attack that exploits trusted relationships among acquaintances.
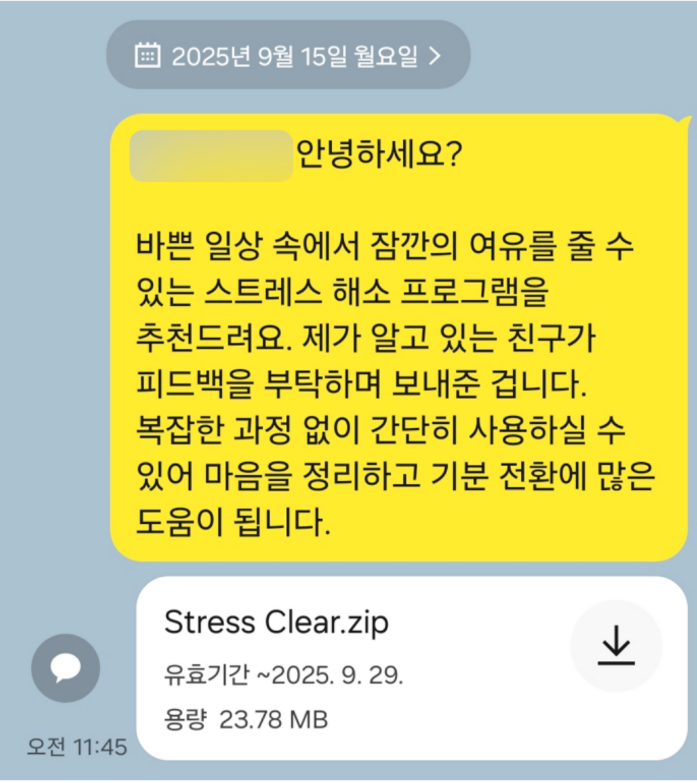 Records of North Korean-backed hackers hijacking victims' KakaoTalk accounts to send malicious files. Genius Security Center
Records of North Korean-backed hackers hijacking victims' KakaoTalk accounts to send malicious files. Genius Security Center
Attacks on Contacts Using Hijacked Accounts: "An Unprecedented Tactic"
This incident revealed an unprecedented attack method. The hacker infiltrated the victim's smartphone and PC, remained dormant for an extended period, and stole account information for Google and major domestic IT services.
The hacker used Google location services on the smartphone to determine when the victim was outside their home or office, then remotely reset the smartphone using Google's "Find My Device Hub" (Find Hub) feature. At the same time, the hacker used infected PCs or tablets at the victim's home or office to distribute malicious code disguised as a "stress relief program" to the victim's contacts.
When some contacts suspected the files were malicious and tried to verify by calling or messaging, the victim's smartphone was in a "system freeze" state, with push notifications, calls, and messages all blocked. This delayed the initial response and allowed the damage to spread rapidly. The hacker also deleted key data such as photos, documents, and contacts from the victims' smartphones, tablets, and PCs.
There is also evidence that the hacker exploited webcams and microphones installed on PCs. The malicious code included functions to control webcams and microphones, raising the possibility that the attacker monitored victims through infected webcams. If the webcam did not have an indicator light, victims likely had no idea that video was being recorded.
As a result, Genius Security Center advised users to use webcams with indicator lights and to physically cover the camera lens when not in use to minimize the risk of hacking. The company also recommended enabling two-factor authentication for logins, refraining from using browser-based password auto-save, and making a habit of shutting down computers when leaving the premises to reduce the risk of both physical and remote attacks.
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.

















