Genians Security Center: "Attack Combined Android Reset and Data Deletion"
Signs of Google 'Find Hub' Feature Abuse... Possible Webcam and Microphone Control
For the first time, evidence has emerged that a hacking group suspected to be backed by North Korea remotely manipulated Android smartphones and PCs to carry out a "destructive cyberattack," completely deleting core data such as photos, documents, and contacts.
According to a threat analysis report released on the 10th by the Genians Security Center, this attack is assessed as the first case where harm was inflicted directly in the real world, going beyond the mere theft of personal information.
The report states that on September 5, a hacker remotely reset the smartphone of a domestic psychological counselor and then used a stolen KakaoTalk account to send multiple malicious files disguised as a "stress relief program" to acquaintances. Ten days later, on September 15, an Android smartphone belonging to a North Korean human rights activist was reset in the same manner, and malicious files were simultaneously distributed through a compromised KakaoTalk account.
While the distribution of KakaoTalk-based malware exploiting trust relationships is a common social engineering tactic used by North Korean hacking groups, this incident revealed an additional attack method not seen before.
The hacker infiltrated the victim's smartphone and PC, remaining dormant for an extended period while stealing Google account credentials and major domestic IT service account information. After verifying that the victim was outside using Google location-based features, the hacker used the Google "Find Hub" function to remotely reset the smartphone. At the same time, infected PCs and tablets left at home or in the office were used to re-distribute malware disguised as a "stress relief program."
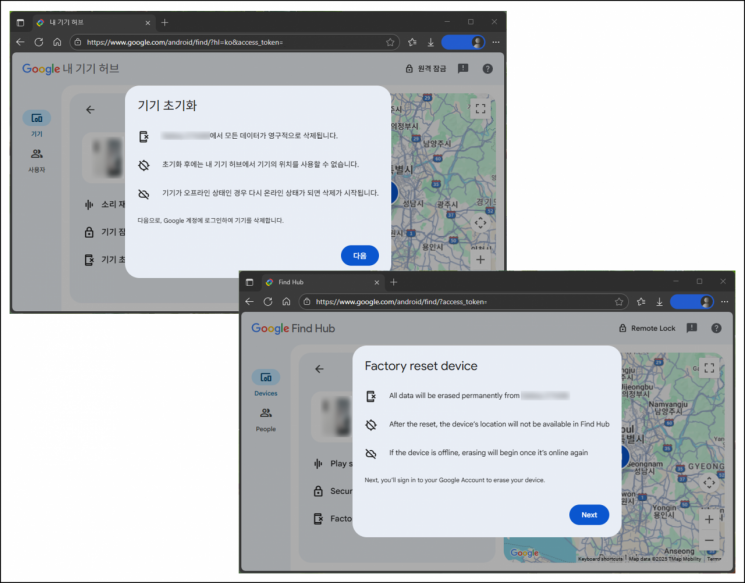 Executing a remote factory reset command on smartphones and tablet devices registered in Google's 'My Device Hub,' showing the device reset command being carried out. Photo by Genius Security Center
Executing a remote factory reset command on smartphones and tablet devices registered in Google's 'My Device Hub,' showing the device reset command being carried out. Photo by Genius Security Center
During this process, the victims' smartphones became completely unresponsive, with calls, messages, and push notifications all blocked. As a result, even if acquaintances noticed something was wrong, they were unable to make contact and could not prevent further damage from spreading.
Additionally, it was confirmed that the hacker deleted core data such as photos, documents, and contacts from the victims' smartphones, tablets, and PCs. Some infected devices were found to have webcam and microphone control features, raising the possibility that the hacker monitored the victims' locations or activities in real time.
Genians noted in the report, "An attack combining device incapacitation and account-based propagation is unprecedented in previous state-backed advanced persistent threat (APT) scenarios," adding, "This demonstrates the tactical maturity of the attack and the advancement of evasion strategies."
The report also emphasized, "It is essential to follow personal security guidelines such as regularly changing your Google account password, enabling two-factor authentication for logins, disabling automatic password saving in browsers, and turning off your PC when not in use."
Previously, the Security Cyber Investigation Unit of the Gyeonggi Nambu Provincial Police Agency announced that it is investigating the hacking case involving the North Korean human rights activist, and confirmed that the structure of the malware used is similar to that previously employed by North Korean hacking groups.
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.

















