With the recent SK Telecom hacking incident and the KT micro-payment case highlighting the importance of mobile communication security more than ever, a domestic research team has become the first in the world to identify a new security vulnerability in LTE core networks.
The LTE core network serves as the backbone that receives signals when mobile phones or Internet of Things (IoT) devices connect to base stations (wireless), verifies user identities, and manages data transmission between users, including internet connectivity, calls, text messages, and billing processes.
The newly discovered vulnerability, identified by the research team, enables an external attacker to remotely manipulate internal information of legitimate users within the LTE core network without authentication.
 (From left) Professor Yongdae Kim of KAIST, PhD candidates Mincheol Son and Kwangmin Kim (co-first authors), (from top left) Professor Chuljun Park of Kyung Hee University, PhD candidate Beomseok Oh of KAIST. Provided by KAIST
(From left) Professor Yongdae Kim of KAIST, PhD candidates Mincheol Son and Kwangmin Kim (co-first authors), (from top left) Professor Chuljun Park of Kyung Hee University, PhD candidate Beomseok Oh of KAIST. Provided by KAIST
KAIST announced on November 2 that the research team led by Professor Yongdae Kim of the School of Electrical Engineering has discovered a new class of vulnerability in LTE core networks called 'Context Integrity Violation (CIV).' Furthermore, they developed 'CITesting,' the world's first systematic tool to detect this vulnerability.
The team's findings were presented at the recently held 32nd ACM CCS (Conference on Computer and Communications Security), where they received the Distinguished Paper Award. ACM CCS is one of the world's top four security conferences, and this year, 30 out of approximately 2,400 submitted papers were selected for awards.
Previous security research has primarily focused on downlink vulnerabilities, where the network attacks the device. In contrast, this study concentrated on uplink security analysis, which examines how devices attack the core network-a relatively neglected area until now.
Specifically, the research team defined a new class of vulnerability called 'Context Integrity Violation.' This concept is rooted in uplink security, where a device (or a device manipulated by an attacker) sends a message to the core network via a legitimate base station, causing the message to incorrectly alter the internal state (information) of the user within the network.
This violates a fundamental security principle: 'Unauthenticated messages must not alter the internal system state.'
In the initial versions of the 3GPP (the international standards body that defines operating rules for mobile and wireless networks) standard, such actions were not explicitly prohibited. While the 3GPP standard stipulates that 'messages that fail authentication are not processed,' it lacks clear guidelines on how to handle messages that arrive without any authentication procedure, leaving room for potential issues.
The only prior research, LTEFuzz, was limited to 31 test cases. In contrast, the research team systematically explored a much broader range of 2,802 to 4,626 test cases using CITesting. Additionally, by evaluating four types of open-source and commercial LTE core networks with CITesting, they demonstrated that real communications could be paralyzed in attack scenarios.
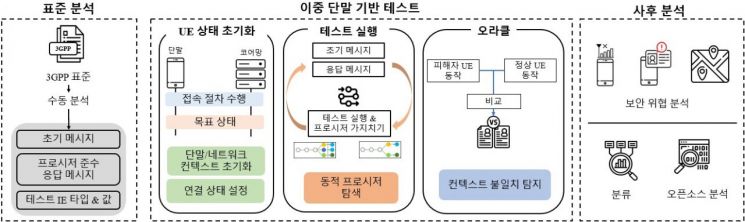 Diagram illustrating the operation process of 'CITesting,' which identifies and detects a new uplink vulnerability called 'Context Integrity Violation' in LTE core networks. Provided by KAIST
Diagram illustrating the operation process of 'CITesting,' which identifies and detects a new uplink vulnerability called 'Context Integrity Violation' in LTE core networks. Provided by KAIST
Through this, the research team confirmed the existence of context integrity violation vulnerabilities and demonstrated that such vulnerabilities could lead to: ▲ 'Denial of service,' where an attacker impersonates a victim's identifier to corrupt network information and deny re-access; ▲ 'IMSI leakage,' where a device is exposed to resend the user's unique identifier (IMSI) stored in the SIM card in plain text; and ▲ location-tracking attacks, where an attacker manually intercepts signals generated when reconnecting with a known permanent identifier to track a specific user's location.
For example, while previous fake base station or signal jamming attacks required physical proximity to the victim, this new attack method involves sending manipulated messages to the core network via legitimate base stations. As a result, it can affect victims remotely from anywhere within the same MME (Mobility Management Entity) jurisdiction-a central controller in LTE networks responsible for subscriber authentication and mobility/session management-making the threat much more widespread, according to the research team.
Professor Kim warned, "Uplink security has long been neglected due to the difficulty of core network testing, lack of implementation diversity, and regulatory issues. As a result, context integrity violations can pose serious security risks."
He added, "Based on the CITesting tool and verification results developed during this research, our team plans to expand the verification scope to 5G and private 5G environments. In particular, we aim to develop CITesting into an essential testing tool that can proactively prevent critical security threats, such as tank communication disruption or IMSI leakage, in industrial and infrastructure-dedicated networks (private 5G)."
This research was conducted by Mincheol Son and Kwangmin Kim, PhD candidates at KAIST's School of Electrical Engineering, as co-first authors; Beomseok Oh, PhD candidate at KAIST's School of Electrical Engineering; Chuljun Park, Professor at Kyung Hee University; and Yongdae Kim, Professor at KAIST, as corresponding authors. The results were presented on October 14 at ACM CCS 2025, held from October 13 to 17 in Taipei, Taiwan.
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.
![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)















