Plenary Session Held on the 27th to Announce Investigation Results and Disciplinary Measures
Multiple Malicious Programs Installed... Missed Opportunities for Prevention
Koh Haksoo: "Security Should Be Recognized as an Essential Investment"
SK Telecom has been fined approximately 134.8 billion won by the government for a personal data leak caused by a hacking incident in April. This is the largest penalty ever imposed for a violation of the Personal Information Protection Act. It was revealed that SK Telecom neglected basic security measures such as encryption, antivirus installation, and security updates, and that the Chief Privacy Officer (CPO) had only limited authority for oversight and management.
On the 27th, the Personal Information Protection Commission held a plenary meeting and imposed a fine of 134.791 billion won and an administrative penalty of 9.6 million won on SK Telecom. This is the highest amount ever, surpassing the total of 100 billion won imposed on Google and Meta in 2022.
Regarding this incident, the Commission classified it as a "very serious violation," the highest level in its criteria for determining fines. Fines can be imposed up to 3% of sales revenue, excluding revenue unrelated to the leak.
Koh Haksoo, Chairperson of the Personal Information Protection Commission, explained, "The company was exposed to vulnerabilities over several years, and there were a very wide range of weaknesses," adding, "Multiple provisions of the regulations were violated, leading us to conclude that this was 'very serious.'"
 Privacy Protection Commission Chairman Koh Haksoo is striking the gavel before deliberating the disciplinary measures for SK Telecom, where a USIM hacking incident occurred, at the plenary meeting held at the Government Seoul Office in Jongno-gu, Seoul on August 27, 2025. Photo by Cho Yongjun
Privacy Protection Commission Chairman Koh Haksoo is striking the gavel before deliberating the disciplinary measures for SK Telecom, where a USIM hacking incident occurred, at the plenary meeting held at the Government Seoul Office in Jongno-gu, Seoul on August 27, 2025. Photo by Cho Yongjun
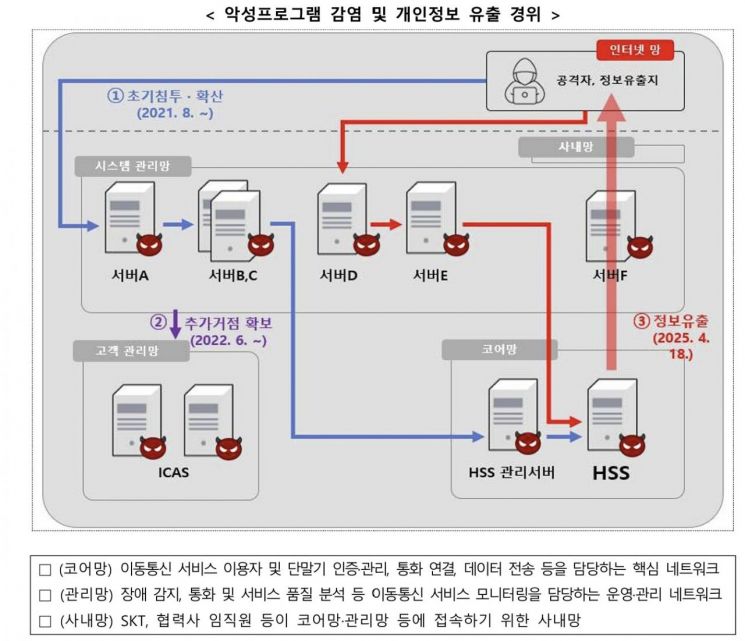
Through a three-month intensive investigation, the Commission confirmed that information from 23,244,649 users (including MVNO users) of SK Telecom's LTE and 5G services was leaked, including phone numbers, subscriber identification numbers (IMSI), USIM authentication keys, and 25 types of data in total.
The initial breach of SK Telecom's internal network by hackers occurred in August 2021, when malicious programs were installed on multiple servers. In June 2022, additional malware was installed in the Integrated Customer Authentication System (ICAS), establishing further footholds. Subsequently, on April 18, 2025, the hackers leaked users' personal information stored in the Home Subscriber Server (HSS) database. The HSS is an authentication system for subscribers to access the mobile communication network.
The Commission stated that this incident "occurred due to SK Telecom's lack of basic security measures and poor management," and added, "The security environment between the internet and the internal network was managed in a way that made it highly vulnerable to illegal intrusion by hackers."
SK Telecom Neglected Access Control and Detection of Illegal Data Exfiltration Attempts
SK Telecom operated its internet, management, core, and internal networks as a single network, allowing unrestricted access from domestic and international internet networks to SK Telecom's internal management servers. Furthermore, the management servers were allowed to connect with the HSS, where the data leak occurred, even though such interconnection was unnecessary. As a result, hackers were able to access the HSS from the internet and transmit USIM information and other data externally.
SK Telecom also failed to monitor abnormal activity logs from its intrusion detection system, neglecting to detect and respond to illegal data exfiltration attempts. Notably, even after confirming in February 2022 that hackers had accessed the HSS server, SK Telecom did not check for abnormal communication, additional malware installations, or the adequacy of access control policies, thereby missing the opportunity to prevent the data leak in advance.
SK Telecom stored files containing account information (IDs and passwords) on management servers without encryption, and allowed personal data to be accessed from the HSS without password input or any authentication process. As a result, hackers were able to use the stolen account information to access management servers, install malware, and retrieve and extract personal information.
Poor Management of Security Updates and Antivirus Installation ... Limited CPO Authority
SK Telecom also failed to properly implement basic security updates. The security vulnerability in the operating system (DirtyCow) that hackers exploited to install malware had already been flagged with a security alert in October 2016, and a security patch had been released. Despite being aware of this, SK Telecom installed an OS with this vulnerability in November 2016 and did not apply the security update until the data leak in April 2025.
 Koh Haksoo, Chairperson of the Personal Information Protection Commission, is attending and speaking at the SK Telecom sanction review held at the Government Seoul Office in Jongno-gu, Seoul on the 27th. 2025.8.27 Photo by Jo Yongjun
Koh Haksoo, Chairperson of the Personal Information Protection Commission, is attending and speaking at the SK Telecom sanction review held at the Government Seoul Office in Jongno-gu, Seoul on the 27th. 2025.8.27 Photo by Jo Yongjun
Since 2020, various commercial antivirus programs have been able to detect the exploitation of this vulnerability, but SK Telecom did not install them until April 2025. The company also failed to implement alternative security measures to compensate for the lack of antivirus protection, ultimately failing to prevent the data leak.
Additionally, SK Telecom stored 26,144,363 USIM authentication keys in plain text without encryption, allowing hackers to obtain the original keys that could be used for USIM cloning. This was despite the fact that LG Uplus had encrypted and stored USIM authentication keys since 2011 and KT since 2014, a fact known to SK Telecom, which failed to take similar measures and thus could not prevent the leak.
The infrastructure involved in this data leak was found to be an area where the CPO had no understanding of how personal data was handled, meaning that the CPO's oversight and management were effectively nonexistent. In addition, the Commission decided to impose an administrative penalty of 9.6 million won for SK Telecom's delayed notification to customers, which failed to prevent further damage.
The Commission held a total of four preliminary review meetings among its members regarding the investigation results and the direction of disciplinary measures. During the plenary meeting, SK Telecom representatives attended to present their views and answer questions, after which the final disciplinary action was confirmed.
To prevent recurrence, the Commission ordered SK Telecom to thoroughly review the handling of personal data across all mobile communication services, strengthen safety measures, and revise its governance structure so that the CPO can oversee all personal data processing work throughout the company.
Chairperson Koh stated, "I hope this incident serves as a turning point for operators who hold and process large-scale personal data to view investments in related budgets and personnel not as mere expenses, but as essential investments."
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.