A security vulnerability has been discovered that can paralyze a commercial smartphone with just a single packet (the unit of data transmission in a network). Experts warn that the severity is extremely high, especially because the discovered vulnerability could potentially lead to remote code execution (RCE). This has prompted calls for the evolution of systematic security inspection frameworks in tandem with increasing technological complexity.
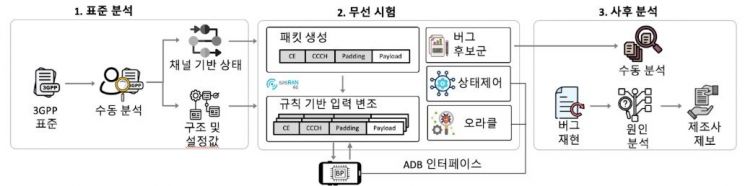
On July 25, KAIST announced that a research team led by Professor Kim Yongdae from the School of Electrical Engineering at KAIST and Professor Park Chuljun from Kyung Hee University has discovered security vulnerabilities in the lower layers of smartphone communication modems using their self-developed analysis framework, 'LLFuzz (Lower Layer Fuzz)'.
 (From left) Yongdae Kim, Professor, Department of Electrical Engineering, KAIST; Tuan Dinh Hoang, PhD Candidate; Taekyoung Oh, PhD Candidate; Cheoljun Park, Professor, Kyung Hee University; Insu Yoon, Professor, Department of Electrical Engineering, KAIST. Provided by KAIST
(From left) Yongdae Kim, Professor, Department of Electrical Engineering, KAIST; Tuan Dinh Hoang, PhD Candidate; Taekyoung Oh, PhD Candidate; Cheoljun Park, Professor, Kyung Hee University; Insu Yoon, Professor, Department of Electrical Engineering, KAIST. Provided by KAIST
Smartphones operate while connected to mobile communication networks. The key component enabling constant connectivity is the communication modem (Baseband) inside the device.
The joint research team used the LLFuzz analysis framework to discover a critical security vulnerability in the lower layers of smartphone communication modems, where a single manipulated wireless packet can paralyze smartphone communications.
The method involves comparing and analyzing the state machines defined by '3GPP' (the international cooperation body that establishes global mobile communication standards) with the actual device responses, allowing precise extraction of implementation vulnerabilities caused by errors.
Through this experimental approach, the team discovered a total of 11 vulnerabilities in 15 commercial smartphone models from global manufacturers including Apple, Samsung Electronics, Google, and Xiaomi.
Of these, 7 vulnerabilities have been assigned official CVE (Common Vulnerabilities and Exposures) numbers. Manufacturers are currently applying security patches for these vulnerabilities. However, the remaining 4 vulnerabilities have not yet been disclosed.
While previous security research has mainly focused on the upper layers of mobile communication, such as the Network Access Stratum (NAS) and Radio Resource Control (RRC), the joint research team concentrated on analyzing the error-handling logic in the lower layers of mobile communication, which manufacturers have relatively neglected.
The identified vulnerabilities occurred in the lower layers of the communication modem, and these areas are structurally susceptible to malfunction from external signal injection because encryption and authentication are not applied.
The lower layers of the communication modem, including RLC, MAC, PDCP, and PHY, refer to the lower layers of LTE and 5G communications, and are responsible for wireless resource allocation, error control, encryption, and physical layer transmission.
The joint research team released a demonstration video showing that when a manipulated wireless packet (malformed MAC packet) generated on a test laptop is injected into a commercial smartphone via a Software-Defined Radio (SDR) device, the smartphone's communication modem (Baseband) immediately ceases to function.
In the video, while the fast.com page is transmitting data at a normal rate of 23MB per second, the transmission stops immediately after the manipulated packet is injected, and the mobile signal disappears entirely. This intuitively demonstrates that a single wireless packet can paralyze the communication modem of a commercial device.
The vulnerability was found in the 'modem chip', a core component of smartphones responsible for calls, messaging, and data communication.
The problematic modem chip (communication component) is not only used in premium smartphones but is also widespread in budget smartphones, tablets, smartwatches, and Internet of Things (IoT) devices. The joint research team warned that this broad distribution could significantly increase the potential for user damage.
The team also conducted experimental vulnerability testing on the lower layers of 5G. Within just two weeks, they identified two vulnerabilities. This result was obtained even without a comprehensive vulnerability assessment of 5G, raising concerns that many more vulnerabilities may exist in the lower layers of the baseband chip's mobile communication stack.
Currently, the joint research team is conducting further analysis of the 5G lower layers using the LLFuzz analysis framework, and is also developing tools for testing the upper layers of LTE and 5G. They are also pursuing collaborations to release these tools in the future.
Professor Kim Yongdae stated, "The lower layers of smartphone communication modems do not apply encryption or authentication, which means that devices are structurally at risk of accepting arbitrary external signals." He added, "This research demonstrates the necessity of standardizing security testing for mobile communication modems in smartphones and other IoT devices."
Currently, security testing for mobile communication modems is standardized only for conformance testing under normal conditions, and there is no standard yet for handling abnormal packets.
Meanwhile, this research was conducted with support from the Institute for Information & Communications Technology Planning & Evaluation, funded by the Ministry of Science and ICT. The first author of the research paper is Tuan Dinh Hoang, a doctoral student at the School of Electrical Engineering at KAIST. The research paper is scheduled to be presented next month at 'USENIX Security 2025', one of the leading international conferences in the field of cybersecurity.
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.
![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)















