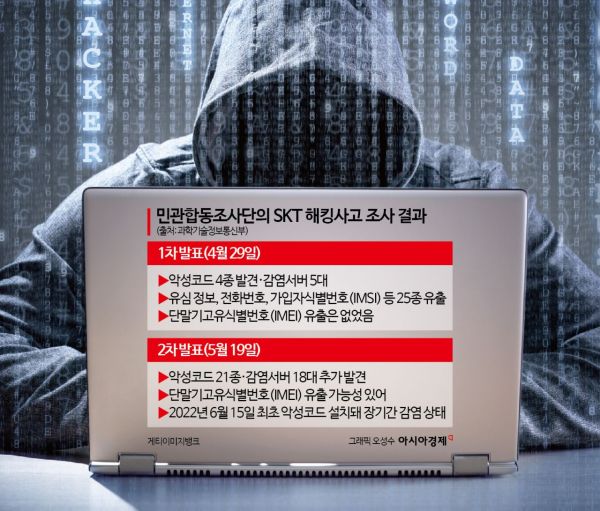
Second Joint Public-Private Investigation Announcement on SKT Breach
21 Types of Malware and 18 Additional Infected Servers Discovered
"Server Temporarily Storing 290,000 IMEI Files Found Infected"
Government Orders SKT to Implement Subscriber Protection Measures
Final Damage Assessment Expected by June
One month after the SK Telecom USIM hacking incident, the government has, for the first time, raised the possibility of cloned phones. Previously, both the government and SKT had maintained that even if USIM information was leaked, it would not be possible to create cloned phones because the device's unique identifier (IMEI) had not been compromised. However, the government has now officially mentioned the possibility of IMEI being leaked externally. SKT, which had emphasized that its USIM protection service alone would prevent any subscriber damage, is now expected to place greater emphasis on USIM replacement.
On May 19, the joint public-private investigation team announced the results of its second investigation into the SKT security breach, revealing that some servers used for customer authentication had been infected with malware, and that personal information such as IMEI, names, and phone numbers had been temporarily stored on those servers.
Malware Infection in June 2022... Possibility of IMEI Leak Raised
The joint investigation found that this server had been infected with malware for an extended period, dating back three years. According to the investigation, there was no evidence of external leakage from December 3, 2024, when log records are available, until April 24, immediately after the hacking incident. However, for the period from June 15, 2022, to December 2, 2023?approximately a year and a half?there are no log records at all, making it impossible to rule out the possibility of IMEI leakage. A senior official from the Ministry of Science and ICT explained, "We have determined that there was no leak during the period when communication logs are available, but we cannot know what happened before that. This means that a new risk of leakage has been identified."
The IMEI is a unique identifier assigned to each device, serving a role similar to a resident registration number for mobile phones. It is highly sensitive information and a critical key for creating cloned phones. In addition to the IMEI, creating a cloned phone requires the subscriber identification number (IMSI) and a cloned USIM. The leak of IMSI and USIM information was already revealed during the first investigation results at the end of last month. With the second investigation now raising the possibility of IMEI leakage as well, there are growing concerns that financial crimes such as "SIM swapping"?a method in which hackers exploit stolen information to clone a USIM and use it in another device for illegal activities?could become a reality.
Eighteen Additional Infected Servers... Investigation to Conclude in June
The second investigation revealed that a total of 18 additional servers had been infected with malware. Among these, the server most problematic was the one integrated with SKT's unified customer authentication system, because key information such as IMEI was temporarily stored during the device authentication process. Files containing a total of 291,831 IMEIs were found on this server.
In the first announcement last month, the joint public-private investigation team stated, "IMEI was not leaked." In this investigation, however, the possibility of IMEI leakage was raised. A Ministry of Science and ICT official explained, "In the first investigation, we urgently checked 38 servers identified as storing IMEI, and since these servers were not infected, we could state definitively that 'there was no leak.' However, during the comprehensive inspection of more than 30,000 servers this time, we found additional servers that temporarily stored IMEI during service operations."
The government has notified SKT of these findings and ordered immediate action. At present, the safest method is to replace the USIM. This involves invalidating the unique identifier of the existing USIM and replacing it with a new one, which can fundamentally block threats such as cloned phone creation or illegal authentication bypass. In contrast, the USIM protection service detects and blocks abnormal activities such as hacking or cloning attempts in real time. However, if the USIM has already been exposed, its actual protective capability may be limited. As of May 18, only 2.1 million SKT subscribers?less than 10% of the total?had replaced their USIMs.
A Ministry of Science and ICT official stated, "We have strongly demanded that the company strengthen its response systems, such as the FDS (Fraud Detection System), which determines the effectiveness of the USIM protection service, and the company is preparing countermeasures." The joint public-private investigation team plans to complete its investigation of all SKT servers by June and to determine the final scale of the damage and the leak routes.
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.


![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)















