Phone Numbers, IMSI, and USIM Management Information Leaked
"No Unique Device Identifiers Leaked... Low Risk of SIM Swapping"
Four Types of Backdoor Malware Discovered on SKT Servers
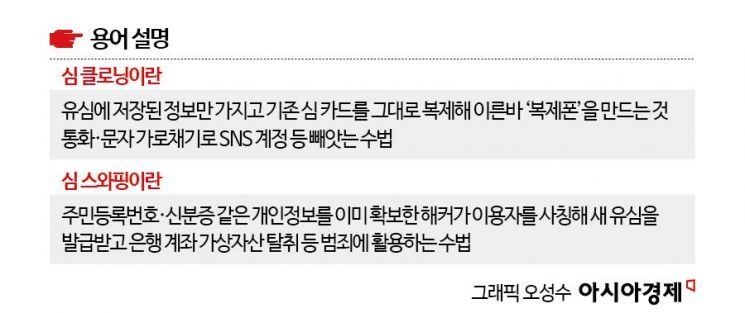
It has been found that information that could be exploited for USIM cloning, such as subscriber phone numbers and subscriber identification keys (IMSI), was leaked in the hacking incident at SK Telecom (SKT), where USIM (Universal Subscriber Identity Module) data was compromised. However, as the unique device identifiers (IMEI) were not leaked, concerns over so-called 'SIM swapping' are considered to be low.
On April 29, the Ministry of Science and ICT announced these initial findings from the joint public-private investigation team regarding the SKT security breach.
According to the investigation team, a total of four types of information that could be used for USIM cloning, including subscriber phone numbers and subscriber identification keys, were found to have been leaked from SKT. In addition, 21 types of SKT management information necessary for processing USIM data were also leaked.
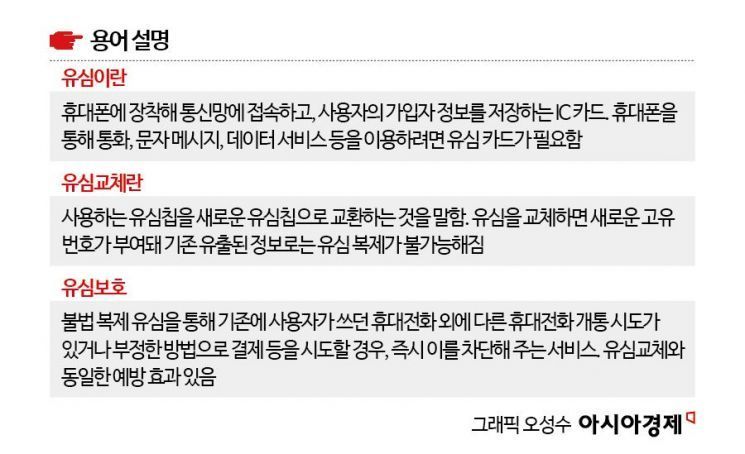
However, it was confirmed that no unique device identifiers were leaked. The unique device identifier serves as a kind of serial number assigned to each device, functioning similarly to a resident registration number for mobile phones. Therefore, the Ministry of Science and ICT explained that subscribing to SKT’s USIM Protection Service can prevent SIM swapping.
SIM swapping refers to the act of cloning a USIM to steal calls, text messages, and even financial information sent to a user’s number. Since unique device identifiers were not leaked, it is possible to detect cloned USIMs by comparing the unique device identifiers of devices attempting to access the network with the registered user information in the system.
Additionally, during the investigation, the team discovered four types of malicious code belonging to the 'BPFdoor' family, which were used in the intrusion. BPFdoor is a backdoor that exploits the network monitoring functionality built into the Linux operating system (OS) to bypass normal authentication procedures. BPFdoor malware is highly covert, making it difficult to detect the hacker's communications. To prevent further spread of the damage, the investigation team shared related information with private companies and organizations on April 25.
So far, the investigation team has examined five servers across three types that showed signs of attack at SKT. The investigation is currently being expanded to include other servers containing important information.
An official from the Ministry of Science and ICT stated, "To minimize public anxiety and damage caused by the USIM data leak, we are actively recommending USIM replacement and encouraging subscription to the USIM Protection Service, which offers equivalent preventive benefits." The official added, "We have completed discussions with service providers to ensure that, from the moment a reservation or application for the USIM Protection Service is made, the service provider will assume 100% responsibility as if the service has already been activated, and this policy will be implemented immediately."
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.