North Korean Hacking Group Sent 126,000 Spoofed Emails in Two Months
Over 17,000 Recipients Targeted; 120 Victims Suffered Personal Data Breaches
It has been confirmed that North Korea was behind the mass distribution of emails impersonating "martial law documents," targeting domestic figures in the fields of unification, security, and diplomacy following the December 3 Martial Law last year. North Korea sent various types of spoofed emails, including those impersonating martial law documents, resulting in 120 individuals actually entering their account information and subsequently having their personal data stolen.
On April 15, the National Police Agency’s National Investigation Headquarters announced that the email incident titled "Disclosure of Martial Law Documents Authored by the Defense Counterintelligence Command," which occurred in December last year, was identified as the work of a North Korean hacking organization.
The police secured multiple key pieces of evidence proving that this incident was carried out by a North Korean hacking group. These include the reuse of servers previously employed in past North Korean hacking cases, the fact that the main recipients were concentrated among defense and diplomatic officials, and that the IP addresses used in the attack were traced to Liaoning Province, a region bordering China and North Korea. Additionally, numerous North Korean-specific terms such as "pogu" (port), "gidong" (operation), and "peji" (page) were found in the internet search records.
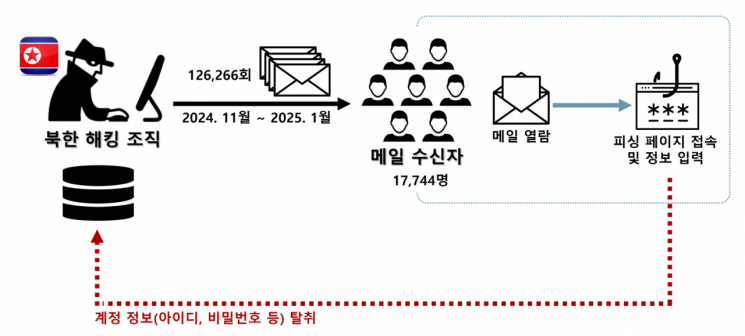 Overview of North Korea-originated Spoofed Email. National Police Agency, National Investigation Headquarters
Overview of North Korea-originated Spoofed Email. National Police Agency, National Investigation Headquarters
The types of spoofed emails sent were not limited to martial law documents. It was revealed that from November last year to January this year, the North Korean hacking group sent a total of 126,266 spoofed emails in 30 different forms-including martial law documents, invitations to concerts by famous singers, and tax refund notices-with the intent of stealing personal information. Out of the 17,744 recipients of these emails, 120 individuals fell victim to personal data breaches after accessing phishing sites and entering their IDs, passwords, and mobile phone numbers.
The North Korean hacking group used 15 servers rented overseas and their own custom programs to send the spoofed emails. These emails were disguised to appear as if they came from public institutions or acquaintances, and the spoofed websites used addresses similar to those of well-known portals to deceive recipients. When recipients clicked on the links, they were directed to phishing sites prompting them to enter their portal IDs and passwords.
An official from the National Police Agency advised, "Do not open emails from unknown senders, and avoid clicking on attachments or links. Always check the website address carefully before entering your ID and password, and conduct regular checks to prevent your account information from being exposed."
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.