First Confirmation of 'Joint Attack'
Difficult to Assess Scale of Damage
It has been confirmed that North Korean hacking groups have launched all-out hacking attacks for at least one year and six months with the common goal of stealing domestic defense technology. Among a total of 83 domestic defense companies, about 10 were hacked, but the exact scale of the damage has not yet been estimated.
The National Police Agency’s National Investigation Headquarters Security Investigation Bureau announced on the 23rd that, as a result of an investigation conducted in cooperation with the National Cyber Crisis Management Group, it was the first time to confirm that North Korean hacking groups Lazarus, Andariel, and Kimsuky jointly attacked with the aim of stealing domestic defense technology.
During the process of confirming the flow of North Korea’s hacking operations, the police recognized that about 10 domestic defense companies were hacked based on their own intelligence obtained and cyber threat information shared among related agencies.
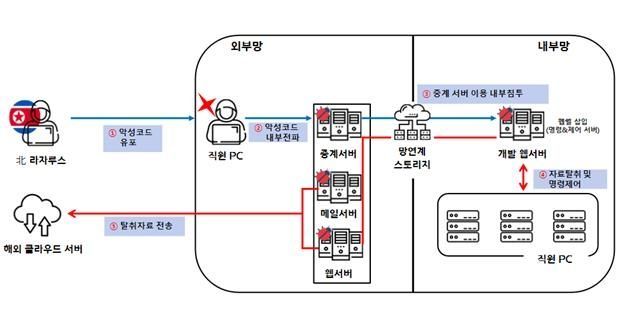
The police regard the attacks as the work of North Korean hacking groups based on the IP addresses used in the attacks, malware such as Nukesped and Tiger RAT, and the method of exploiting software vulnerabilities to build relay servers.
In some cases of damage, specific IP details were confirmed in the Shenyang area of China, which turned out to be the same IP used in the 2014 Korea Hydro & Nuclear Power attack.
The North Korean hacking groups mainly infiltrated defense companies directly but also approached defense subcontractors with relatively weak security. They hacked subcontractors to steal server account information of defense companies, then illegally infiltrated main servers to distribute malware.
The attack methods varied by hacking group.
Lazarus hacked the external network server of defense company A from November 2022, infected it with malware, and then took control of the company’s internal network through ports of a network linkage system open for testing purposes. Subsequently, they collected important data from six internal network computers, including those of development team employees, and transferred it to overseas cloud servers.
Andariel stole account information of company C, which remotely maintains and services defense subcontractor B and others, from around October 2022, installed malware on servers of B and others, and extracted defense technology data. It was investigated that Andariel obtained personal commercial email account information of C’s employees, accessed the corporate email, and stole sent and received materials. This exploited the vulnerability that some employees used the same ID and password for commercial email accounts and internal work system accounts.
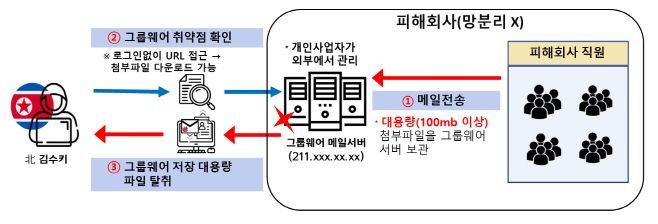
Kimsuky exploited a vulnerability in the email server of defense subcontractor D from April to July last year, which allowed downloading large files sent and received by email externally without login, to steal technical data.
The police confirmed through this investigation that hacking attacks occurred from at least one year and six months ago until relatively recently, but it is difficult to grasp the exact period of the crime and the overall scale of the damage.
An official from the National Investigation Headquarters explained, "We estimated the damage period for each case by partially confirming the stolen information on overseas cloud servers, but it is difficult to specify the overall crime period due to reasons such as the retention period of communication logs and deletion of theft traces." He added, "The scale of the damage will be examined in depth by the Ministry of National Defense and the Defense Acquisition Program Administration, which are the management and supervisory agencies."
The police suspect that there was a specific directive from North Korean State Affairs Commission Chairman Kim Jong-un behind this incident.
An official from the National Investigation Headquarters said, "It was previously known that Kimsuky mainly attacked government agencies and politicians, Lazarus targeted financial institutions, and Andariel focused on military and defense agencies, but this investigation confirmed that they launched all-out attacks around the same time with a single purpose." He added, "It was also confirmed in this investigation that the targets of hacking attacks were expanded not only to defense companies but also to subcontractors and maintenance companies."
Meanwhile, regarding the hacking of defense companies, the police said there are no domestic individuals under investigation for supporting North Korea or companies under investigation for negligence in maintaining security. The National Investigation Headquarters stated, "Defense companies cannot be investigated solely based on the fact that they were hacked," and added, "The Defense Acquisition Program Administration will handle the matter according to relevant laws and regulations."
Along with the investigation, from January 15 to February 16, the National Investigation Headquarters conducted joint inspections targeting defense companies in cooperation with the Defense Acquisition Program Administration and the National Intelligence Service to continue additional damage prevention measures.
An official from the National Investigation Headquarters said, "We judge that North Korean hacking groups will continue attacks to steal defense technology," and added, "We plan to strengthen cooperation by signing a business agreement with the Defense Acquisition Program Administration so that not only defense companies but also subcontractors can strengthen their security independently."
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.