Announcement of Investigation Results on the 'Impersonation Email Sending Incident'
The number of victims in the ‘Impersonation Email Incident,’ identified as the work of a North Korean hacking group, has exceeded 1,400.
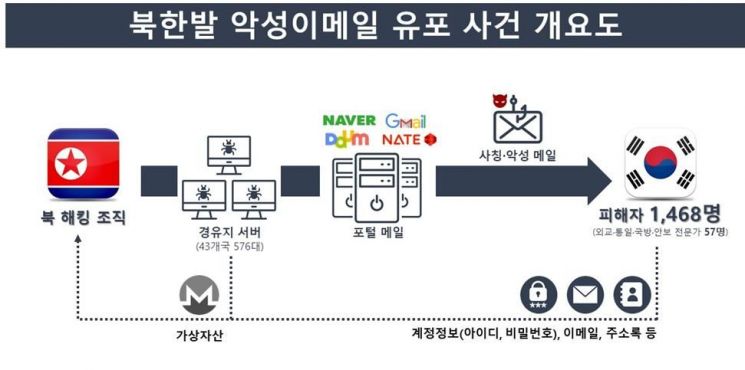
On the 21st, the National Police Agency’s National Investigation Headquarters announced that, after tracking and investigating the ‘Impersonation Email Sending Incident targeting National Assembly offices and journalists,’ they confirmed that impersonation emails have continued to be sent this year as well, expanding the range of targets following last year. The police also identified that this hacking group is stealing virtual assets through various methods.
The North Korean hacking group sends emails disguised as ‘notices’ or ‘inquiries’ that might interest recipients, impersonating government agencies, journalists, and research institutes. When recipients open the attached files in these emails, malicious programs that can leak information from personal computers (PCs) are installed and executed.
Cases were also confirmed where recipients were induced to click on internet addresses (URLs) included in the emails. In these cases, victims were led to fake websites mimicking trusted institutions or portal sites, where their account information was stolen.
In particular, the North Korean hacking group creates websites of the recipient’s affiliated institutions to induce access and conducts specialized attacks tailored to each victim, employing increasingly sophisticated methods.
Through this investigation, the number of email account theft victims was identified as 1,468. Among them, 57 were experts such as current and former officials in diplomacy, unification, defense, and security fields, while 1,411 were general individuals from various occupations including office workers, self-employed, and unemployed persons.
The reason the targets have now expanded beyond specific fields to a broad spectrum is analyzed to be because the North Korean hacking group is targeting virtual assets. Following the first confirmation last year that they distributed ‘ransomware’ to extort virtual assets, this year they attempted unauthorized access to virtual asset exchange accounts of impersonation email victims and secretly ran ‘virtual asset mining programs’ on 147 compromised relay servers.
As the North Korean hacking group recently expanded the targets of impersonation emails and diversified their activities to include virtual asset extortion, theft, and mining, the police have begun sharing information and cooperating with related agencies such as the Ministry of Foreign Affairs, the U.S. government, and the United Nations to actively prevent and block damage. Additionally, the police recommended security measures for email users, collaborated with the Korea Internet & Security Agency to block phishing sites operated by the North Korean hacking group, and provided related information such as the list of relay servers controlled by the group to relevant agencies including the National Cyber Crisis Management Center to aid in establishing information protection policies.
The National Police Agency urged, “As the attacks by the North Korean hacking group are expanding comprehensively, to prevent further damage, passwords for emails and virtual asset exchange accounts should be changed regularly, and security settings such as two-factor authentication, one-time passwords (OTP), and blocking overseas IP addresses should be strengthened.”
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.
![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)















