National Police Agency and National Intelligence Service Recognize Damage Through 'Threat Information Sharing'
North Korea's Attack Methods Becoming More Sophisticated... Request to Block Overseas Access
It has been confirmed that a North Korean hacking group sent malicious emails to 150 current and former high-ranking officials, as well as experts in diplomacy, unification, security, and defense, timed with the launch of the Yoon Suk-yeol administration.
On the 7th, the National Police Agency's National Investigation Headquarters announced that after investigating the malicious email incident targeting key security-related personnel from April to July last year, it was confirmed to be the work of a specific North Korean hacking group. They sent malicious emails that induced access to phishing sites and then stole account information. So far, the police have identified a total of nine victims.
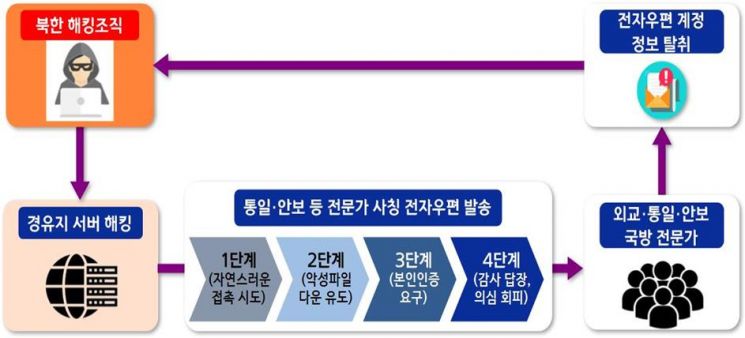
The North Korean hacking group secured a foundation for hacking attacks by taking control of 138 servers through domestic and international hacking and laundered IP addresses to avoid tracking. To evade investigation, they separated servers by function, such as sending malicious emails, building phishing sites, and transmitting stolen information.
National Police Agency and National Intelligence Service Recognize Damage through 'Threat Information Sharing'... Active Damage Response
This incident was recognized through cyber threat information sharing between the National Police Agency and the National Intelligence Service. The Jeju Police Agency, the National Police Agency's Security Investigation Bureau, and the National Intelligence Service, which initially launched the investigation, analyzed and tracked about 5,800 emails and completed protective measures for victims through joint efforts with related agencies.
The National Police Agency considers this incident to be the work of the North Korean hacking group commonly named 'Kimsuky' by domestic and international private security firms. The police based this judgment on factors such as the IP addresses used in the attack, the method of establishing relay points, North Korean-style vocabulary and phrases, and the fact that most targets were experts in diplomacy, unification, security, and defense.
During the investigation, the police discovered a virtual asset wallet address used by the Kimsuky hacking group on the attack server. They believe that attempts to steal money are also underway and are continuing the tracking investigation.
Increasingly Sophisticated ‘North Korean Hacking Attacks’... "Regularly Change Email Passwords"
The police confirmed that the attack methods of the North Korean hacking group are becoming more sophisticated. They analyzed that the group carefully approached by impersonating opinion leaders in the security field using social engineering techniques.
First, they attempt to make the approach as natural as possible from the victim's perspective. When impersonating a journalist, they initially send a legitimate email requesting an interview or materials. After the victim replies, the attacker sends another response to induce downloading a large document file.
The attacker claims that enhanced security requires identity verification to open the document file and directs the victim to a fake phishing site. When the victim enters their ID and password, the attacker steals the account information. Finally, the attacker sends a thank-you reply to the victim to dispel suspicion.
Meanwhile, the National Police Agency expects North Korea's hacking attempts targeting security-related personnel to continue and urges strengthening security measures such as regularly changing email passwords, enhancing biometric authentication settings, blocking overseas access, and rechecking suspicious emails.
A National Police Agency official stated, "We will continue to actively share cyberattack trends and response cases that threaten national security with related agencies," and added, "We plan to strengthen preemptive responses to illegal cyber activities by North Korean hacking groups."
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.

![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)















