Court, Prosecution, Financial Supervisory Service Impersonation... Voice Phishing Crime
Charges Including Distribution of Malicious Programs Under the Information and Communications Network Act
[Asia Economy Reporter Jang Sehee] A voice phishing gang that distributed an app impersonating the Paul AntiSpy app to delete malicious apps and committed fraud to embezzle 6.1 billion KRW has been arrested by the police.
On the 22nd, the Cyber Investigation Division of the National Police Agency's National Investigation Headquarters announced that they had arrested two Koreans and one Chinese on charges of distributing malicious programs under the Information and Communications Network Act, invasion of privacy under the same act, and fraud, and sent them to the prosecution. Among them, one managed voice phishing call center employees, and two were call center employees.
The police reportedly identified and sequentially arrested the suspects over about four years from 2019, immediately after the incident occurred, until March of this year. They were caught by the police while entering Korea from China.
They are accused of impersonating courts, prosecutors' offices, and the Financial Supervisory Service from October 2018 to April 2019, extorting about 6.1 billion KRW from 166 victims under the pretext of protecting deposits. They committed the crime by collecting cash face-to-face from the victims.
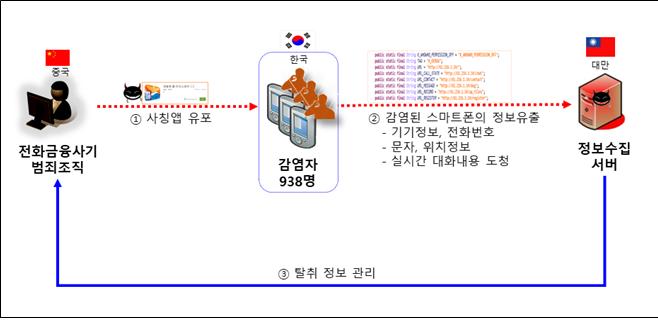
It is also known that they distributed malicious apps impersonating the Paul AntiSpy app to eavesdrop on victims' personal information and call records. It was reported that they tried to preemptively detect victims reporting to the police or banks by installing the malicious app. In this process, they sent fake search warrants and arrest warrants via mail and KakaoTalk notifications to make victims believe they were law enforcement agencies.
A police official stated, "The basic purpose of installing the malicious app was to monitor every move of the victims," and added, "It has been confirmed that they examined call records and location information."
According to the police, the suspects meticulously planned the crime by regularly testing whether the malicious app worked properly using mobile devices directly brought from Korea and encrypting the app itself to hinder tracking.
Meanwhile, the suspect who acted as the cash collector has not yet been arrested.
A police official urged the public to be cautious, saying, "No government agency sends search warrants, arrest warrants, or official documents via message windows like KakaoTalk or social networking services (SNS)."
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.