Kakao Disguise, Phishing Attack Targeting North Korea-Related Workers
"IP Used in Attacks on Diplomacy and Security Personnel"
[Asia Economy Reporter Jang Hee-jun] It has been revealed that a North Korean hacking group sent emails impersonating 'Kakao' in an attempt to steal personal information from individuals working in the diplomatic and security sectors.
Moon Jong-hyun, Director at East Security, stated in a phone interview with Asia Economy on the 25th, "A phishing email disguised as a Kakao login page was discovered," adding, "It appears to have been sent to numerous individuals in the diplomatic, security, and defense fields since the beginning of this month."
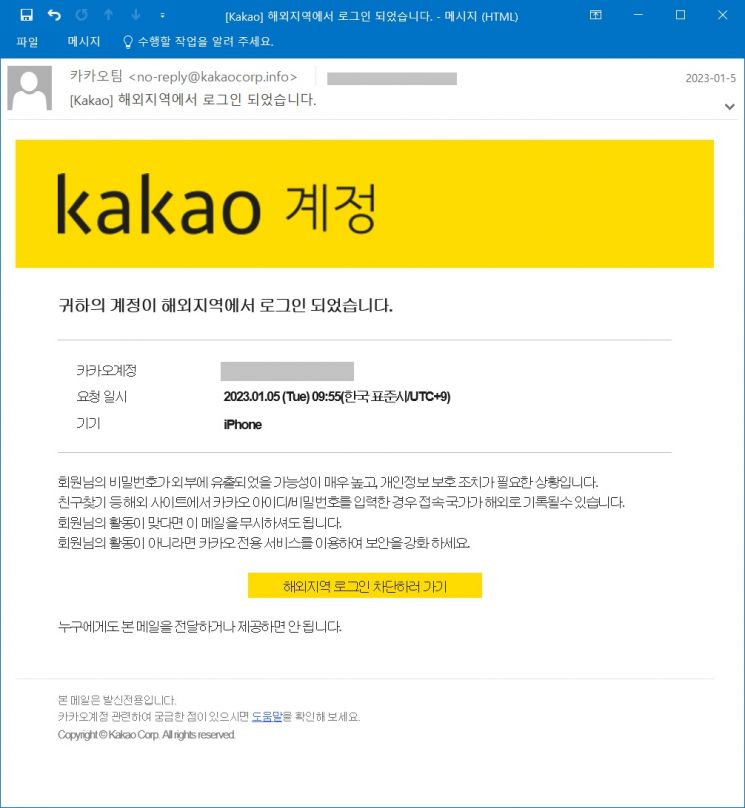
According to the email released by East Security, the sender, presumed to be a North Korean hacker group, impersonated the Kakao team with the subject line '[kakao] Logged in from an overseas location.' The body contained a message stating 'Your account was logged in from an overseas location' along with a button labeled '[Go to block overseas login]'.
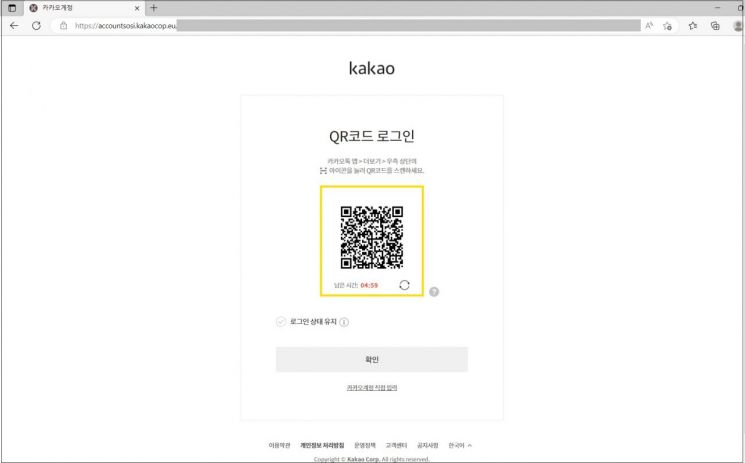
Clicking the problematic button leads to a fake Kakao login page, which is designed to closely resemble the actual Kakao login page. It includes menus for entering ID and password as well as QR code login, and the moment personal information is entered, it is transmitted to the attacker’s server.
After analyzing various indicators, East Security concluded that this attack is an extension of the 'Smoke Screen' attack activities by the APR organization, believed to be backed by North Korea. The IP addresses used in this attack were also utilized in North Korean hacking attempts last month targeting individuals active in the domestic diplomatic and security sectors.
Earlier this month, a hacking group under North Korea’s Reconnaissance General Bureau called 'Kim Su-ki' was detected distributing phishing emails impersonating the portal site 'Daum' operated by Kakao, attempting to steal users’ passwords. This attack was similarly structured to disguise the login page so that when victims entered their personal information, it was sent directly to the hackers’ servers.
Additionally, it has been found that North Korea sent phishing emails to 892 experts in the diplomatic and security fields at least three times last year. When a fire caused a Kakao service outage in October last year, they immediately disguised themselves as an account management service to attempt to steal accounts of defectors and others. Recently, they also carried out attacks impersonating the National Tax Service’s 'Tax Audit Attendance Request Notice.'
Director Moon Jong-hyun said, "The level of the attacks themselves is low, but a significant number of people are falling victim to these routine techniques," emphasizing, "Who receives these attacks is more important than which portal is being impersonated. High-ranking officials working in diplomacy, security, unification, and defense sectors are routinely receiving such emails, so special caution is necessary."
Meanwhile, according to the National Intelligence Service, attempts by international and state-backed hacking groups reach an average of 1.15 million per day. The intelligence authorities believe that many of these are the work of North Korea. The National Intelligence Service expects North Korea’s cyberattacks against South Korea to intensify this year and reports a significant increase in efforts to steal technology related to nuclear power plants and defense industries.
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.
![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)















