"Information Stored in Separate Systems"
Questions Raised About Credibility of Coupang's Statement
Internal Authentication System Neglected for Extended Period
Government Launches Joint Public-Private Investigation Team
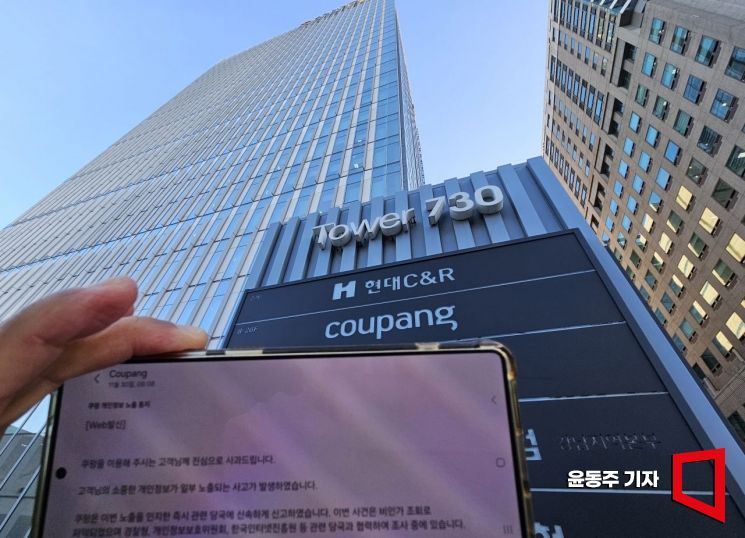 A massive personal information leak involving over 30 million cases has occurred at Coupang. This scale exceeds the economically active population of 29.69 million, making it the worst leak incident in history. On December 1, following an apology text message from Coupang regarding the personal information leak, a Coupang signboard installed at Coupang headquarters is visible. 2025.12.01 Photo by Yoon Dongju
A massive personal information leak involving over 30 million cases has occurred at Coupang. This scale exceeds the economically active population of 29.69 million, making it the worst leak incident in history. On December 1, following an apology text message from Coupang regarding the personal information leak, a Coupang signboard installed at Coupang headquarters is visible. 2025.12.01 Photo by Yoon Dongju
The scale of Coupang's personal information leak has grown to 7,500 times larger than initially announced, prompting the government to investigate the possibility of payment information also being compromised. While the company continues to emphasize that "payment information is safe," the government has stated that it is conducting its own investigation, separate from Coupang's explanations, as various questions have arisen during the revelation of the incident. In particular, concerns have been raised about the credibility of Coupang's statements, as the company admitted that it only became aware of the breach in November, despite evidence that intrusion attempts had been ongoing since the end of June.
An official from the Personal Information Protection Commission stated on December 1, "Coupang claims that payment information and personal information are stored in separate systems," but added, "However, since the investigation is ongoing, it is difficult to accept this claim as definitive."
Previously, Coupang insisted that the information exposed in this breach was limited to names, phone numbers, addresses, emails, and some order details, repeatedly asserting that payment information, credit card numbers, and login credentials are "managed separately in different systems and are therefore safe." Security experts agree that Coupang's explanation is technically plausible, as payment information is more sensitive than general personal information. However, they also point out that while such a structure is possible in theory, it is necessary to independently verify whether this system architecture and access control actually functioned as intended.
In addition to the possibility of further information leaks, questions surrounding the root cause of this incident must also be clarified during the investigation. The discovery of evidence that Coupang's internal authentication system had been neglected for an extended period has further fueled these suspicions. According to data received from Coupang by Assemblywoman Choi Minhee, Chair of the National Assembly's Science, ICT, Broadcasting, and Communications Committee, on November 30, it was confirmed that a signature key (token signature key) issued to authentication-related personnel had remained unrenewed for a long time. If a token is akin to a disposable access pass, the signature key is comparable to the stamp that issues these passes. Even if an access pass is discarded, as long as the stamp itself remains valid, anyone can continue to create new passes at will.
Coupang failed to delete or renew the signature key used to generate tokens when the responsible employee left the company, leaving this long-valid signature key vulnerable to misuse by internal staff (or former employees). While Coupang has not disclosed the exact validity period of the authentication key exploited in the hacking incident, citing the ongoing police investigation, the company responded that "it is common for token signature keys to be set with a validity period of five to ten years."
A more fundamental question is whether Coupang truly failed to detect the mismanagement of authentication keys for five months. Although suspicious access had been ongoing since the end of June, Coupang only recently became aware of the breach, suggesting that basic platform security measures-such as access control, log analysis, and anomaly detection-were not functioning properly. Whether the unauthorized access involved the use of insider privileges, the reuse of a former employee's authentication information from outside, or any other form, the fact that it went undetected for five months is considered technically implausible. It is still unclear whether this detection delay was due to a simple technical failure, or if the company was aware of the breach internally for some time before disclosing it. Professor Yum Heungyeol of Soonchunhyang University's Department of Information Security explained, "If an insider accesses the system in a sophisticated manner, detection can be difficult, but the fact that no signals were detected for five months essentially means the security system was not functioning properly."
If future investigations reveal that payment or credit card information was also leaked, the impact of the incident will inevitably be even greater. This is because the possibility of financial damages, such as fraudulent payments, would become real, and the responsibilities for sanctions or compensation by relevant institutions would also increase.
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.