Cyber Crisis Response Drills Conducted Since 2004
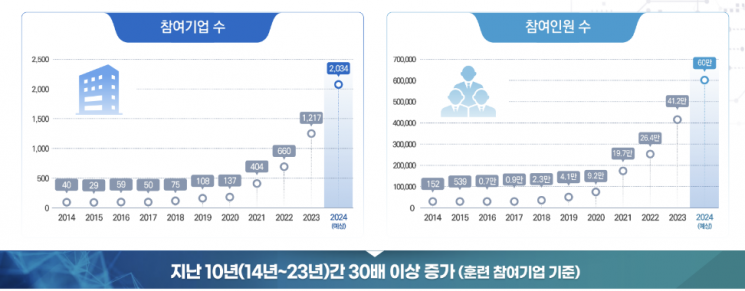
Expected Participation of 2,034 Companies and 600,000 Employees This Year
The number of reported cyber intrusion incidents in South Korea has doubled over the past three years. In response to these threats, the government is conducting free cyber simulation training for small and medium-sized enterprises (SMEs).
On the 9th, the Korea Internet & Security Agency (KISA) projected that a total of 2,034 companies and 600,000 employees would participate in this year's cyber crisis response simulation training.
Since 2004, KISA has been conducting training to enhance organizations' cyber crisis response capabilities by preparing for various attacks using methods identical to actual hacking.
Recently, both the number and scale of cyber threats have been on the rise. Last year, the number of reported intrusion incidents reached 1,227, double the 640 cases reported in 2021. It is expected that the figure for the first half of this year alone, at 899 cases, will far exceed last year's total.
The number of reported server hacking incidents also increased from 166 cases in 2021 to 585 in 2022, and 583 last year, while large-scale DDoS attacks targeting domestic companies are also on the rise.
In particular, many hacks begin with phishing emails that impersonate other organizations to induce clicking on links (URLs) or opening attachments. After infiltrating via phishing emails, hacking progresses through DDoS, web shell, and vulnerability attacks.
Jinwan Park, head of KISA's Intrusion Incident Prevention Team, explained, "As non-face-to-face work increases, damage caused by hacking emails is also rising. Companies are constantly exposed to threats, and SMEs are especially in a blind spot."
A representative case is a large corporation that suffered a loss of 24 billion KRW after being deceived by an email impersonating the oil company Aramco in 2016. Other cases include hacking attacks or financial damages caused by impersonating the Constitutional Court (2019), a UK defense contractor (2021), and the National Election Commission (2022).
Park stated, "Cyber simulation training allows for preemptive response to intrusion incidents and minimizes damage. As it has evolved into continuous and autonomous training centered on companies, the number of participating companies has increased."
It is explained that especially by providing free continuous training to micro and small enterprises, the program helps companies lacking cyber crisis response capacity. The regular training sessions held in the first and second halves of the year have no restrictions on participation, including large corporations and non-profit organizations.
The training covers four areas: hacking emails, DDoS attack response, web vulnerability inspection, and vulnerability detection and response. Participating companies can review their training results, and there is also a debriefing session where outstanding company cases are shared and awarded.
To apply for the service, visit the KISA BohoNara website, apply for the simulation training, and fill out the online application form.
Park said, "The number of companies participating in simulation training has increased more than 30 times over the past 10 years, showing strong industry interest. We hope companies enhance their crisis response capabilities through training that uses methods identical to actual hacking to prepare for cyber threats."
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.