North Korean hacking group 'Andariel' has been detected hacking domestic defense contractors and other entities to steal critical technical data and laundering money by transferring it to their country, prompting the police to launch a comprehensive investigation.
On the 4th, the Security Investigation Support Division of the Seoul Metropolitan Police Agency announced that they conducted raids on a domestic server used as a base by Andariel, a virtual asset exchange, and the residence of a foreign woman identified as Ms. A, through whom the funds flowed. They also carried out multifaceted investigations including digital forensics on Ms. A’s mobile phone and laptop.
From December last year to March this year, Andariel accessed a domestic server rental company used as an intermediary server in Ryugyong-dong, Pyongyang, North Korea, a total of 83 times, utilizing this company as a hacking base. Ryugyong-dong houses the International Communications Bureau and the Pyongyang Information Center. The police confirmed these facts by investigating the Google Mail account used by the hacker while cooperating with the U.S. Federal Bureau of Investigation (FBI), which had been tracking Andariel.
The police seized domestic rental servers and domestic and international emails including Google accounts, and based on subscriber information of the servers, conducted over 40 rounds of communication investigations. They found that Andariel hacked defense contractors, research institutes, pharmaceutical companies, and stole not only critical technical data such as laser anti-aircraft weapons, detectors, and production plans but also personal information including user IDs and passwords of server accounts. The affected companies included subsidiaries of major domestic conglomerates, domestic technical research institutes, educational institutions, and companies in defense, finance, pharmaceuticals, logistics, and IT sectors.
These companies were virtually defenseless against hacking. The police notified the affected companies that a total of 1.2 terabytes (TB) of files presumed to contain critical technologies and data had been stolen, but most of the companies were unaware of the damage. According to the police, some did not report the damage to the police out of concern for corporate reputation decline.
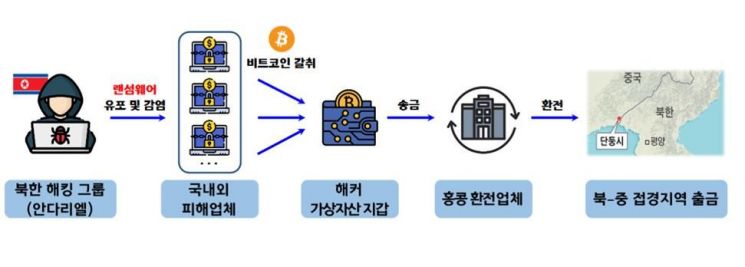
Andariel distributed malicious ransomware that infected computer systems and demanded Bitcoin as a condition to restore access rights. There were three victim companies, with damages amounting to approximately 470 million KRW. The Bitcoins paid by the victim companies passed through domestic virtual asset exchange Bithumb and overseas virtual asset exchange Binance. After seizing and analyzing transaction records from these exchanges, the police found that some of the extorted Bitcoins passed through the account of foreign woman Ms. A and, after money laundering, about 630,000 yuan (approximately 110 million KRW) was remitted to the Chinese K Bank located in Liaoning Province, China. A police official explained, "This money was withdrawn at a branch of K Bank located in the North Korea-China border area," and added, "It is presumed that the funds flowed into North Korea."
The police have registered Ms. A as a suspect and are investigating whether she acted as a money laundering agent for Andariel by seizing and examining about 50,000 files. Ms. A denies the charges, claiming that she only provided her account for convenience while working as an employee at a currency exchange company in Hong Kong in the past. A police official stated, "We will actively conduct international cooperative investigations with related agencies such as the U.S. FBI regarding the overseas attack and damage sites and related parties confirmed in this case," and added, "We also plan to continue investigating additional damage cases and the possibility of similar hacking attempts."
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.

![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)















