Methods Using Email Attachments
Be Cautious of 'Reply·Download'
Recently, cyber attacks via electronic mail (email) have been on the rise, requiring caution. The method involves ransomware or malware being executed when downloading attachments included in emails.
"Interview Request Regarding North Korea's Missile Threat"
 [Image source=Asia Economy DB]
[Image source=Asia Economy DB]
According to Radio Free Asia (RFA) on the 9th, some individuals working in industries related to North Korea received emails from a KBS news bureau reporter specializing in unification and diplomacy on the 7th.
The email titled "KBS Interview Request" contained the message, "We would like to request interviews only with experts holding different perspectives on the rapidly increasing missile threat from North Korea, focusing on Korea-China relations, Korea-Japan relations, North Korean nuclear negotiations, and weapons system development." It concluded by encouraging a reply with, "I am always looking forward to your response."
If a reply is sent to this email, the attacker attempts to send a malicious file only to the respondent. Experts analyzed that North Korea is the entity behind this cyber attack.
Downloading the malicious file sent by the hacker may lead to the leakage of data stored on the computer, and the hacker may also monitor the infected computer.
This attack is characterized by North Korean hackers using a Russian server at the address ‘mpevalr.ria[.]monster’ and impersonating a current KBS reporter. Although the relevant authorities cooperated to block access from Korea to this server, caution is necessary as there is a possibility of modified attacks occurring.
Previously, North Korea attempted hacking by impersonating the National Pension Service and the Cyber Safety Bureau of the National Police Agency.
Emails titled '[Important] Notice from the Cyber Safety Bureau' at the end of last month and '[National Pension Service] Notification to Check Your Subscription Details' earlier this month were revealed to be aimed at stealing recipients' personal information. Experts predicted that these attacks, which stimulate curiosity and anxiety, are typical North Korean hacking methods.
According to the '2022 Year-End Report' published on the 2nd by the U.S. cybersecurity firm Recorded Future, North Korean hacking groups such as 'BlueNoroff (APT38)' and 'Lazarus' have conducted extensive cyber attacks and are expected to actively engage in cyber attacks this year as well.
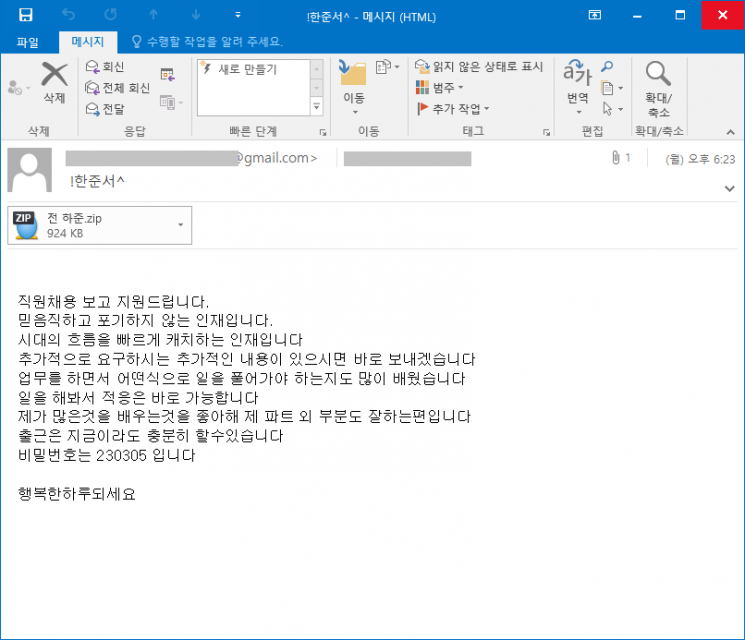
"Contacting You Regarding the Job Posting"
 [Image source=Asia Economy DB]
[Image source=Asia Economy DB]
Hacking attacks disguised as recruitment are also taking place.
On the 8th, East Security's Security Response Center (ESRC) warned that Lockbit ransomware and Vidar malware are being distributed through phishing emails disguised as job applications.
Ransomware is a compound word of ransom and software. Hackers use it to disable files or systems and then demand money as a condition to unlock them.
The main targets of this ransomware attack were public enterprises. They sent emails to HR personnel of companies that posted job openings with messages such as "Contacting you regarding the job posting" and "Interviews or starting work are possible at any time," attaching compressed files resembling job applications.
After downloading the compressed file and unlocking it with the password provided in the email body, icons of Hangul files or Excel files appear. However, these are 'exe' executable files with only the icons changed. Changing the file icon is used to induce downloads.
If the user runs the file to check the job application, ransomware is installed on the computer.
The ransomware encrypts all local drives on the user's computer, connected network shared drives, and shared folders, changing the file extensions to 'Lockbit.' It not only makes file recovery difficult but also creates ransom notes and changes the desktop wallpaper. Only then does the user realize that their computer has been infected with ransomware.
There is another type of attack. Similarly disguised as a job application, it distributes a variant of the information-stealing malware called 'Vidar.' When the user runs this file, the computer connects externally, and a series of programs are installed on the computer. Subsequently, the hacker steals various information stored on the computer.
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.


![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)














