[Asia Economy Reporter Seungjin Lee] AhnLab announced on the 28th the latest phishing email threat trends by analyzing phishing emails collected over the past month in preparation for the year-end and New Year period when email traffic increases.
Be cautious of subject lines with 'Re', 'order', and 'payment'
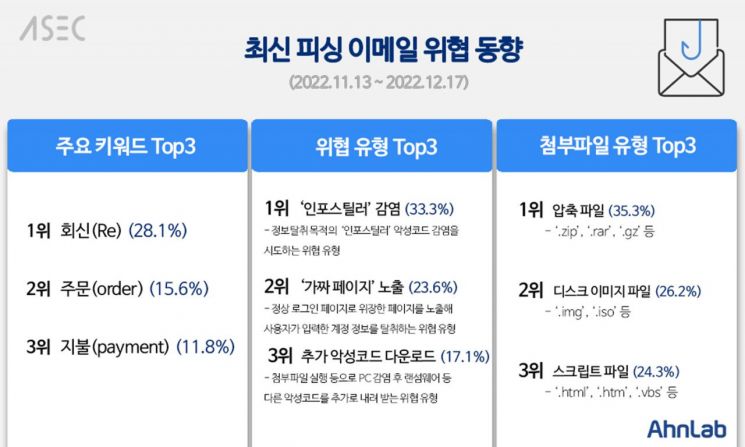
The most frequently used keyword by phishing email attackers over the past month was ‘Re’, accounting for 28.1% of the total. Attackers mainly prefixed ‘Re’ to the email subject line. Next was ‘Order’, meaning order, at 15.6%, ranking second, followed by ‘Payment’ at 11.8%, ranking third.
The most common ‘Re’ is presumed to be frequently used by attackers because recipients may mistakenly believe the phishing email is a continuation of a previous conversation. The following keywords ‘order’ and ‘payment’ reflect the recent trend of increasing online financial transactions both domestically and internationally, interpreted as attempts to attract users’ attention.
Information theft malware infections most common
AhnLab’s analysis showed that threats attempting to infect ‘infostealer’ malware for information theft purposes accounted for the highest proportion at 33.3% of phishing email attacks. Next was the ‘fake page’ exposure type, which displays fake login pages indistinguishable from legitimate ones by including malicious scripts in attachments, at 23.6%. The ‘additional malware download’ type, which infects PCs through attachment execution and then downloads other malware, ranked third at 17.1%.
Infostealers are frequently used by attackers because they extensively steal user information stored in web browsers such as portal and company system login credentials, emails, virtual asset wallets, and files, which can directly cause financial damage.
Beware of attachments like '.zip, .rar, .gz'
Among the types of attachments used by attackers, ‘compressed files’ such as '.zip, .rar, .gz' ranked first at 35.3%. Next were ‘disk image’ files with extensions like '.img, .iso' at 26.2%. ‘Script’ files with extensions such as '.html, .shtml, .htm, .vbs' ranked third at 24.3%.
Recently, attackers have recognized that companies mainly use spam mail filtering systems that automatically block emails with executable files attached, so they mainly use compressed file formats or disk image file formats to conceal malicious executable files. Additionally, attackers use script files to expose ‘fake login pages’.
To prevent damage from phishing emails, it is essential to follow basic security rules such as ▲carefully verifying email senders ▲not opening attachments or URLs in suspicious emails ▲avoiding saving passwords in web browsers and regularly changing passwords ▲keeping antivirus programs like V3 updated and enabling phishing site blocking features ▲maintaining the latest versions and security patches of programs in use (OS/internet browsers/office software, etc.).
Kim Geon-woo, head of AhnLab Security Emergency Response Center (ASEC), emphasized, “Malware distribution and information theft attempts using phishing emails have long been favored methods by attackers. Recently, these methods have become more sophisticated, so users should make it a habit to follow security rules such as not executing URLs and attachments in emails from unknown sources.”
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.
![Clutching a Stolen Dior Bag, Saying "I Hate Being Poor but Real"... The Grotesque Con of a "Human Knockoff" [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)















