Chainalysis 2021 Analysis Report
[Asia Economy Reporter Minyoung Cha] Last year, the estimated global damages from ransomware attacks amounted to approximately $602 million (about 732.9 billion KRW). Amid the escalating armed conflict between Ukraine and Russia this year, signs of cyberattacks targeting Ukraine, presumed to be backed by Russia, were also detected last year.
According to the industry on the 5th, blockchain data platform company Chainalysis estimated the ransomware damages for the year 2021 at about $602 million in its recently released '2022 Virtual Asset Crime Report' ransomware edition.
Considering damages that have not been precisely identified, the total damage is expected to be even greater. For example, the damage in 2020 was estimated at about $692 million as of January 2022, nearly double the estimate published in the 2021 Virtual Asset Crime Report.
The ransomware group that caused the most damage last year was Conti, which extorted more than $180 million. Next was DarkSide, which attacked the U.S. Colonial Pipeline oil pipeline company. The number of ransomware variants active in 2021 was at least 140, up from 79 in 2019 and 119 in 2020.
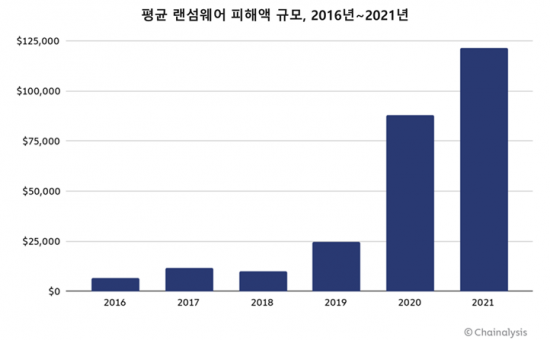
The average damage per ransomware incident continues to increase. Last year, it was $118,000 per case, steadily rising from $25,000 in 2019 and $88,000 in 2020. This is because ransomware attackers are focusing on large-scale organizations as primary targets and have enhanced the effectiveness of their attacks by using third-party rented infrastructure, hacking tools, and stolen data.
Most ransomware uses the method of laundering funds by sending the proceeds to centralized exchanges. Chainalysis analyzed that since 2020, 56% of funds transferred from ransomware addresses moved to six virtual asset companies, indicating that the ransomware ecosystem is smaller than expected.
The motives vary. While most attacks are financially motivated, some have geopolitical objectives. These focus on deception, espionage, defamation, and disruption of enemy state information governance. In the past year, ransomware attacks linked to Iran surged, and in January, hackers associated with the Russian government were detected attempting attacks against Ukrainian government agencies, according to Chainalysis.
Many cases of rebranding were also found. Rebranding refers to ransomware attackers publicly ceasing operations and then resuming under a new name. Notably, the Russia-based cybercrime group Evil Corp is believed to have rebranded many ransomware variants such as Phoenix Cryptolocker and Grief.
Baek Yong-gi, head of Chainalysis Korea, said, “Ransomware is the most dynamic and constantly evolving virtual asset-based crime. Law enforcement agencies and cybersecurity experts must continuously monitor ransomware that demands assets linked to dark coins like Monero or other protocols with enhanced privacy features and adapt investigative methods accordingly.”
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.

!["The Woman Who Threw Herself into the Water Clutching a Stolen Dior Bag"...A Grotesque Success Story That Shakes the Korean Psyche [Slate]](https://cwcontent.asiae.co.kr/asiaresize/183/2026021902243444107_1771435474.jpg)















