Conducting Second Half-Year Simulation Training for 285 Private Companies
[Asia Economy Reporter Minyoung Cha] As hacking incidents increase worldwide, security vulnerabilities were found in the web and business servers of 60% of companies that participated in the second half of last year's cyber simulation training.
The Ministry of Science and ICT announced the results of the 2021 second half cyber crisis response simulation training conducted for private companies in cooperation with the Korea Internet & Security Agency on the 17th.
This second half simulation training was conducted over about three weeks starting November 1 last year, targeting 285 private companies and 93,257 employees. The scale increased by 48.4% and 8% respectively compared to the first half of last year. Compared to the 2020 annual average, it increased by 3.5 times and 2.1 times respectively.
The purpose of the training was to check employees' procedures for responding to hacking emails, verify recovery status following DDoS attacks, and confirm exposure to security threats through simulated penetration testing on company websites and servers.
During the training, the government sent hacking emails impersonating recent issues or internal employees, such as 'program update notifications' and 'in-house COVID-19 vaccination candidate notices,' to employees. The emails induced installation of malware by clicking on attachments during the reading process.
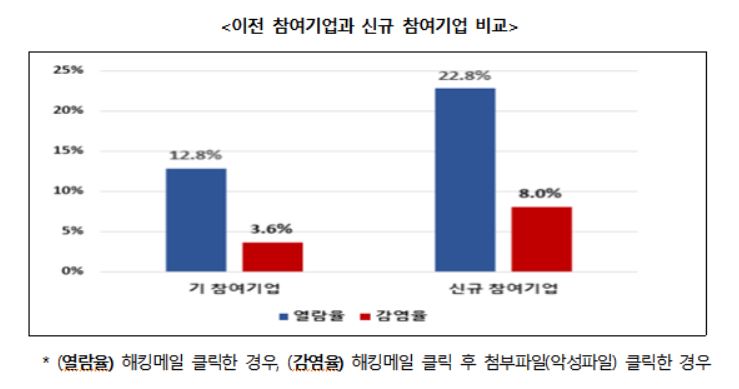
The overall hacking email open rate was 16.7%, and the infection rate was 5.4%, which decreased by 9.1 percentage points and 2.2 percentage points respectively compared to the first half of last year (25.8%, 7.6%). In particular, the infection rate of companies participating again in the training was 3.6%, which was 45% lower than the 8.0% infection rate of newly participating companies. The government also conducted information security education on ransomware cases, prevention rules, and recovery procedures.
Small and medium-sized enterprises (SMEs) were more vulnerable to security compared to large companies with security investment capacity. Large companies shortened the time to detection by about 4 minutes and response by about 7 minutes compared to the first half. The government judged that SMEs were insufficient in DDoS attack types and log analysis and conducted training to improve the response capabilities of security personnel. It also guided the use of remote security monitoring and KISA’s DDoS Cyber Shelter.
Vulnerabilities were also revealed in simulated penetration training using white-hat hackers. White-hat hackers found and removed 163 web vulnerabilities on the websites of 40 out of 45 companies. On web and business servers, security vulnerabilities were found and removed in more than half of the 50 participating companies, specifically 32 companies.
Hong Jin-bae, Director of the Information Security Network Policy Division, said, “Recently, a critical vulnerability was discovered in Apache Log4j, increasing cyber threats worldwide. We urge many companies to actively participate in the government’s simulation training to identify and address cyber threat vulnerabilities in advance to minimize damage.”
Meanwhile, the Ministry of Science and ICT plans to develop and promote scenarios focusing on threat responses such as increased threats targeting Internet of Things (IoT) devices, theft of metaverse user information, and unauthorized sales after unauthorized access related to Non-Fungible Tokens (NFTs) in this year’s cyber crisis response simulation training. They will build a customized continuous hacking simulation training platform and guide participating companies to specify this in their information security disclosures.
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.