APT37 Distributes Emails Impersonating US Human Rights Groups
Suspected Attempt to Steal Information from North Korea Defectors and Activists
Malware Spread Targeting 'Itaewon Disaster' in South Korea
A North Korean hacker group has been found to have set up a phishing site disguised as a prominent 'North Korean Human Rights' organization with the aim of stealing personal information. The hacker group in question previously distributed malware through a disguised file containing the response situation during the so-called 'Itaewon disaster' last October.
According to the Genieon Security Center on the 1st, the North Korean hacker group 'APT37' sent emails disguised as a guide to the North Korean human rights activity support program of the U.S.-based nonprofit organization Liberty in North Korea (LiNK) to multiple North Korea activists on July 24.
 North Korean hacker organization
North Korean hacker organization
The email claimed to recruit participants for the 'Changemaker Activity Support Fund Program' actually operated by Liberty in North Korea, enticing defectors and related organization officials by instructing them to refer to the website for details. Clicking the homepage link at the bottom of the email leads to a phishing domain, and entering information there results in theft by the attacker group. The center traced the flow of the base server and confirmed that it was connected to the APT37 infrastructure.
The center explained that the hacker group directly built the domain and web server used as the attack base and used a 'Browser-in-the-Browser' technique that inserts a manipulated popup window inside the web browser for authentication purposes. The conclusion is that the attack is a 'cyber espionage' aimed at stealing personal information while monitoring the daily lives of North Korea experts. A center official warned, "Be aware that if the popup window cannot be moved outside the browser screen, it is not a real window."
APT37, the group that spread malware during the 'Itaewon disaster'
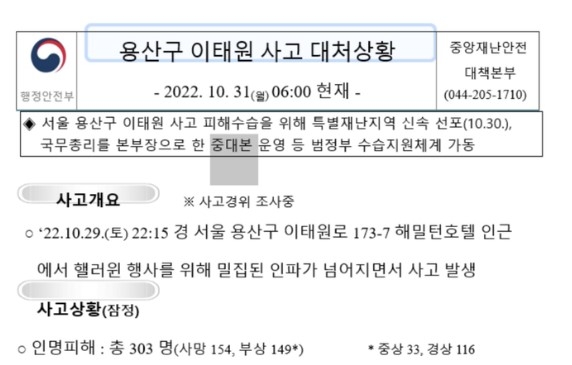 North Korean hacking group 'APT37' impersonates Itaewon disaster report to distribute malware [Image source=Google Threat Analysis Group (TAG)]
North Korean hacking group 'APT37' impersonates Itaewon disaster report to distribute malware [Image source=Google Threat Analysis Group (TAG)]
The North Korean hacker group APT37 primarily collects confidential information and has attacked North Korea-related organizations and defense sector personnel. It is also known as Geumseong121, Skarkraft, RedEyes, and Group123. In 2019, it distributed malware embedded in emails disguised as explanatory materials from the Ministry of Unification, and in 2018, it spread malicious files for smartphones disguised as the Naver Vaccine app.
Notably, APT37 also distributed malware embedded in a Word file titled 'Yongsan-gu Itaewon Accident Response Situation - 2022.10.31 (Mon) 06:00 Current' as recently as last October. The problematic file was found to be crafted by imitating the Central Disaster and Safety Countermeasures Headquarters report format. It contained detailed information on the actual accident overview, casualties, and response status.
Not only the Itaewon disaster but also recently, North Korea has shown behavior that meticulously exploits social issues in South Korea. Earlier in October, when a fire at the SK C&C Pangyo data center caused Kakao service disruptions, phishing emails titled '[Kakao] Partial Service Error Recovery and Emergency Measures Notice' were sent to North Korea-related industry workers, defectors, and politicians.
North Korean hacker group even creates real-time fake 'Naver' sites
North Korea also set up phishing sites that replicate the widely used domestic portal site 'Naver' in real time. Instead of the legitimate domain address (www.naver.com), domains such as 'www.naverportal.com' were used to attempt hacking against unspecified many. Earlier, the National Intelligence Service detected such attack signs in June and immediately took blocking measures.
North Korea had previously simply replicated the login pages of portals like Naver and Kakao to induce domestic users to log in. This was an attempt to hack IDs and passwords to steal personal information. However, the problematic site detected by the National Intelligence Service was found to have completely replicated the actual Naver main screen in real time. Even detailed menus such as stocks, real estate, and news were implemented identically.
An official from the National Intelligence Service explained, "It is difficult to distinguish the phishing site from the actual site just by appearance," and added, "It appears that North Korea has evolved its attack methods to increase the possibility of stealing personal information." He further urged, "As North Korea's hacking attack methods targeting our citizens are becoming increasingly sophisticated, we ask for heightened vigilance."
© The Asia Business Daily(www.asiae.co.kr). All rights reserved.












